
- Amber Smith
- September 19, 2024
What is a Crypto Wallet?
A crypto wallet is used to interact with a Blockchain network. The three major types of crypto wallets are hardware, software, and paper wallets. Based on their work, they can be further classified as cold or hot wallets. Software-based wallets are more accessible and more convenient, whereas hardware ones are the most secure. Paper wallets are printed out on paper and are now unreliable and obsolete. In reality, crypto wallets don’t store the currency but act as a tool of interaction with Blockchain, i.e., generating the necessary information to receive and send money via Blockchain transactions.
The information comprises pairs of private and public keys. Based on these keys, an alphanumeric identifier called address is generated. In essence, this address specifies the location to which coins can be sent to the Blockchain. The address can be shared to receive funds, but private keys are to be never disclosed. The private key can be used on any wallet for accessing the cryptocurrency. As long as the private key is known, funds are accessible on any device. Also, coins are just transferred from one address to another, never leaving the Blockchain..
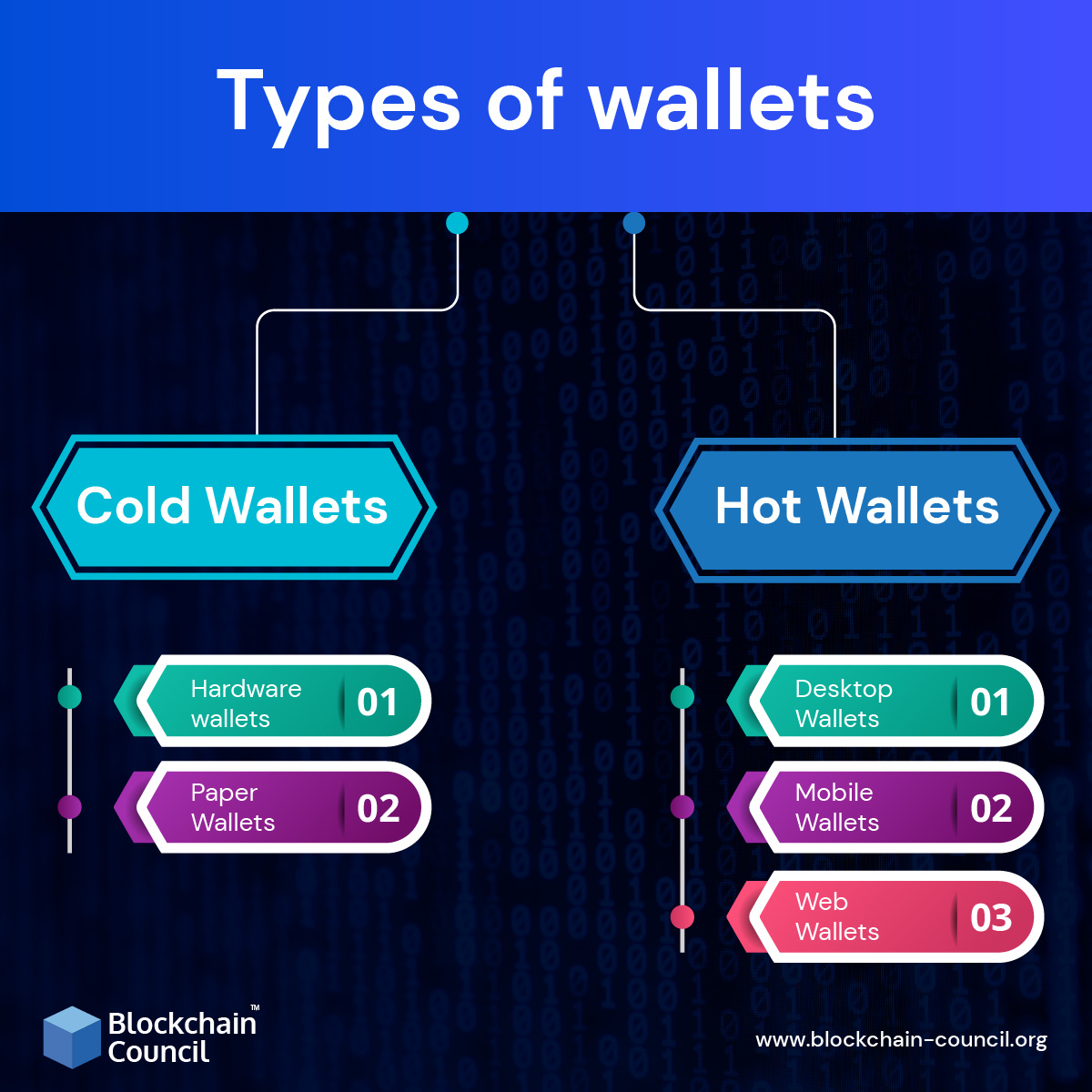
Types of Wallets
A wallet is a combination of a public address and a private key. The wallets can be categorized based on the method and location of storage in the following segments. Crypto wallets can broadly be categorized into cold wallets and hot wallets:
Hot and Cold Wallets
Internet connectivity defines a wallet in terms of hot or cold. Hot wallets are connected to the Internet and thus are less secure and pose more risks but are user-friendly. Cold wallets, on the other hand, are stored offline and don’t require internet connectivity. Thus, improving security and less risk. When compared to a safe or a vault, more substantial sums of money can be stored than that in a carry-around wallet. Hot wallets are more likely to be used for daily transactions, and cold wallets for more long-term holdings. Hot wallets are easy to set up, and the funds are quickly accessible. Traders conveniently use them. Cold wallets are hack resistant, and thus the cold storage is suitable for HODLers. As a protection method, only a small percent is stored in hot wallets while being able to trade directly from their cold storage devices..
Hardware wallets
Hardware wallets are hardware devices that individually handle public addresses and keys. It looks like a USB with an OLED screen and side buttons. It is a battery-less device and can be connected to a PC and accessed by native desktop apps. It costs up to 70-150 dollars, but it is worth it. They have received a mixed response. They are more secure than hot wallets and user-friendlier than paper wallets but less than web and desktop wallets. They are available in different forms and offer reasonable amounts of control. They are difficult for beginners to use when the investment is significant. The Most popular hardware wallets are Ledger Nano S and Trezor.
Paper Wallets
It is a physically printed QR coded form wallet. Some wallets allow downloading the code to generate new addresses offline. They are not prone to hacks, but the number of flaws has made them dangerous. A major flaw is not being able to send partial funds. Thus, it can’t be reused. They used to be very popular for cold storage, but not after hardware wallets came onto the scene. All in all, if stringent security precautions are taken, then paper wallets can be set up.
Desktop Wallets
These are installable software packs available for operating systems and are becoming serious with time. Anti-virus is required because a system connected to the Internet poses fundamental security issues. Instead of keeping cryptos on an exchange, desktop wallets for bitcoins should be used. They are the third most secure way to store cryptocurrencies and the best method for cold storage in a completely clean system. They are easy to use, give privacy and anonymity, and involve no third party. Regular backing up of the computer is needed. Popular desktop wallets are Exodus, Bitcoin core, Electrum, etc.
Mobile Wallets
Mobile wallets are just like desktop wallets made for smartphones. They are quite convenient as it uses QR codes for transactions. They are suitable for daily operations but are vulnerable to malware infection. Encryption of mobile wallets is necessary. They are practical and can be used on the go but open to viruses. Some mobile wallets are Coinomi and Mycelium..
Web Wallets
As the name suggests, these wallets are accessed by internet browsers. The private keys are held in some web wallets and are prone to DDOS attacks. They can be hosted or non-hosted. Non-hosted is preferred as funds are always in control. They are the least secure wallets. They are not the same as hot wallets. They are ideal for small investments and allow quick transactions. Some of these are MetaMask and Coinbase.
Custodial Wallets and Non-Custodial Wallets
In addition to hot and cold wallets, it’s essential to understand the difference between custodial and non-custodial wallets.
Custodial Wallets
- Third-Party Control: Custodial wallets are provided by third-party service providers, such as cryptocurrency exchanges or online wallet platforms. These providers take care of managing your private keys and the security of your cryptocurrencies on your behalf.
- User-Friendly: Custodial wallets are often designed to be user-friendly, making them a suitable choice for beginners or those who prefer a more straightforward approach to managing their digital assets. They are generally easier to set up and use.
- Recovery Options: Many custodial wallet providers offer account recovery options in case you forget your password or lose access to your account. This can be convenient, but it also means that the service provider has a level of control over your assets.
- Risk Factors: The main risk with custodial wallets is that the service provider can be a target for hackers. If the provider’s security is breached, your funds could be at risk. Additionally, the service provider may have terms and conditions that could affect your access to your funds.
- Examples: Some examples of custodial wallets include wallets provided by popular cryptocurrency exchanges like Coinbase, Binance, and Kraken.
Non-Custodial Wallets
- Full Control: Non-custodial wallets provide you with complete control over your private keys and, consequently, your cryptocurrencies. You are responsible for the security and management of your assets.
- Enhanced Security: Non-custodial wallets prioritize security and privacy. Since you hold the private keys, it’s less likely that your funds will be compromised through a breach of a third-party service. This makes them a preferred choice for individuals who value security.
- Privacy and Anonymity: Non-custodial wallets are known for offering a higher level of privacy and anonymity. Your financial transactions and holdings are not subject to the data collection practices of third-party providers.
- Self-Responsibility: While non-custodial wallets offer more control, they also require users to take responsibility for their private keys and ensure they are kept secure. Losing access to your private keys can result in the loss of your funds, with no recovery options.
- Examples: Examples of non-custodial wallets include hardware wallets like Ledger Nano S and Trezor, as well as software wallets like Electrum, MyEtherWallet, and Trust Wallet.
The choice between custodial and non-custodial wallets depends on your preferences and priorities. If you value convenience and are willing to trust a third party with your assets, custodial wallets may be suitable. However, if you prioritize security, privacy, and full control over your cryptocurrencies, non-custodial wallets are the way to go. It’s essential to choose a wallet type that aligns with your specific needs and the level of control you want over your digital assets.
How Does Crypto Wallets Work?

When you buy cryptocurrency, you receive a wallet, often referred to as a hot wallet. This wallet is online and connected to the internet. Think of it like your everyday bank account, where you can access your funds.
Now, to enhance security, you can opt for a cold wallet, which is like a digital vault. It’s offline, not connected to the internet, making it resilient to hackers. To safeguard your assets, you transfer them from your hot wallet to your cold wallet.
A key concept to understand is that cryptocurrencies aren’t physically stored anywhere; they exist as data on a Blockchain. Your wallet serves as the keeper of the keys – a public key (like your account number) and a private key (similar to a bank card’s PIN).
Much like how a PIN is required to access your bank account, the private key is essential for accessing your cryptocurrency on the Blockchain. Without it, you can’t conduct transactions.
Your wallet software uses these keys to interact with the Blockchain. When you want to send cryptocurrency, you enter the recipient’s address, specify the amount, sign the transaction with your private key, add a transaction fee, and confirm the send. Receiving works the same way – the sender uses your address, and you accept the payment.
High-risk wallets
Now that we know the different types of crypto wallets, let’s understand why it is crucial to protect them:
- The LastPass Incident: In October 2023, hackers executed a heist, draining approximately $4.4 million from 25 LastPass users. They exploited vulnerabilities in the wallet system, affecting 80 to 85 distinct wallets. The key takeaway here is that even well-known wallet providers can fall victim to breaches. Robust security measures are your best defense.
- BitForge Vulnerabilities: Major wallet providers, including Coinbase, Binance, and ZenGo, found themselves vulnerable to a series of cryptographic protocol flaws collectively termed “BitForge.” These issues allowed attackers to access entire private keys, putting user funds at risk. The incident underscores the importance of continuous security updates and patching.
- The MetaMask Incident: On April 19, 2023, MetaMask users reported a significant hacking incident. Attackers compromised Ethereum wallets, resulting in the loss of millions of dollars. While the specifics of this exploit were debated, one thing was clear: no wallet is entirely immune to threats. Your wallet’s security is ultimately in your hands.
- Phishing Attacks: Phishing attacks are a devious way cybercriminals trick crypto owners into revealing their private information. Hackers poses as trusted entities approach crypto enthusiasts. Take Dominic Lacovone, for instance, who encountered fraudsters masquerading as Apple Support. They cunningly obtained access to his iCloud account, where he stored his MetaMask recovery phrase. In mere minutes, they siphoned off $650,000. This real-world example underscores the importance of staying vigilant and not falling for seemingly harmless traps.
- Vulnerable Key Management Systems: The choice of whether wallet providers keep mnemonic keys in their servers can affect security. In the case of the Slope wallet hack of 2022, they retained users’ mnemonic keys in their logs. Hackers identified this vulnerability and plundered over $4 million of users’ funds. This example reminds us that if keys must be stored, they should be in a secure environment, scrutinized by third-party auditors.
When it comes to safeguarding your digital assets in the realm of cryptocurrencies, knowledge about crypto wallet security is paramount. In this subsection, we will delve into some real-world examples of crypto wallet security measures that can make the difference between keeping your assets safe and being vulnerable to potential threats.
How to protect crypto wallets? Crypto Wallet Security Tips
Let’s understand how you can ensure the security of your crypto wallet.
| Security Tip | Description |
| Hardware Wallets | Use physical devices (e.g., Ledger, Trezor) to keep keys offline for maximum security. |
| Two-Factor Authentication (2FA) | Enable 2FA for extra login protection by requiring a mobile-generated code. |
| Multi-Signature Wallets | Employ multi-signature wallets for shared accounts, reducing single points of failure. |
| Secure Passwords | Use strong, unique passwords and consider password managers. |
| Seed Phrase Backup | Safely store offline as a recovery key, split it for added security. |
| Cold Storage | Keep assets offline in ‘cold wallets’ like paper wallets. |
| VPN for Extra Shielding | Use a VPN for encryption and privacy while accessing your wallet. |
| Multiple Wallets | Diversify assets across various wallets for risk reduction. |
| Trusted Sources | Buy hardware wallets from reputable vendors or official sources. |
| Secure Environment | Use secure, malware-free devices and avoid risky actions. |
Hardware Wallets
Hardware wallets are the gold standard in crypto security. They are physical devices designed to keep your private keys offline, making them virtually immune to online threats. Brands like Ledger and Trezor offer top-notch security with a user-friendly interface.
Two-Factor Authentication (2FA)
Enabling 2FA adds an extra layer of protection to your crypto wallet. It requires you to provide not only your password but also a unique code from your mobile device for login. This double-check system helps deter unauthorized access.
Multi-Signature Wallets
Multi-signature (multi-sig) wallets demand multiple private keys to authorize a transaction. They’re ideal for shared or business accounts, as they ensure no single point of failure.
Secure Passwords
Using strong, unique passwords for each wallet is fundamental. Password managers like LastPass can generate and store complex passwords, reducing the risk of unauthorized access.
Seed Phrase Backup
Never underestimate the importance of your seed phrase. Safely store it offline, as it’s your recovery key. Splitting it in two secure locations adds an extra layer of protection.
Cold Storage
Storing your assets in a ‘cold wallet’ means they are disconnected from the internet, making them impervious to online attacks. Paper wallets are a classic example, offering offline security.
VPN for Extra Shielding
Using a VPN (Virtual Private Network) while accessing your crypto wallet provides encryption for your online activities. It masks your location and protects you from potential prying eyes on public networks.
Multiple Wallets
Diversifying your assets across various wallets is like spreading your risk. If one wallet faces issues, your other assets remain safe, reducing potential losses.
Trusted Sources
Only obtain hardware wallets from reputable vendors or official sources. Avoid third-party sellers to minimize the risk of compromised devices.
Secure Environment
Using a secure, malware-free device and avoiding risky actions, like installing unknown apps or clicking on suspicious links, keeps your wallet environment safe.
Investigate the efficiency of cryptowallets in the high-transaction environment
You can choose the type of crypto wallet as per your needs, but remember to back it up regularly and use the latest software. If you are interested in learning more, you can sign up for cryptocurrency certification courses online.
FAQ’s
What are the different types of crypto wallets?
- There are three major types of crypto wallets: hardware, software, and paper wallets.
- These wallets can be further categorized as hot or cold based on their internet connectivity.
What is a crypto wallet?
- A crypto wallet is a tool used to interact with a Blockchain network.
- It holds pairs of private and public keys, which are essential for cryptocurrency transactions.
What is a hot wallet?
- A hot wallet is a type of crypto wallet that is connected to the internet.
- Hot wallets are more accessible and user-friendly but are considered less secure compared to cold wallets.
- They are often used for daily transactions and quick access to funds.
What is a cold wallet?
- A cold wallet is a type of crypto wallet that is offline and not connected to the internet.
- Cold wallets are highly secure and less susceptible to hacking.
- They are typically used for long-term storage of cryptocurrencies.
What are the features of a crypto wallet?
- A crypto wallet holds a public key for receiving funds and a private key for access and transactions.
- It allows users to send and receive cryptocurrencies by signing transactions with their private keys.
- Wallets can be categorized based on their internet connectivity (hot or cold) and the method of storage (hardware, software, or paper).
- Some wallets offer features like two-factor authentication (2FA), multi-signature support, and recovery options to enhance security and usability.
How lost btc wallets can influence?
Lost BTC wallets have a multifaceted impact: financially, individuals face irrecoverable losses as the bitcoins in these wallets become permanently inaccessible. This reduction in accessible bitcoins also affects the overall Bitcoin supply, potentially leading to a decrease in circulation. Over time, this can exert upward pressure on Bitcoin’s price due to the increased scarcity. Additionally, the loss of wallets highlights significant security vulnerabilities, urging users to adopt more stringent security measures. These incidents serve as a sober reminder of the risks associated with managing digital assets.





































































 Guides
Guides News
News Blockchain
Blockchain Cryptocurrency
& Digital Assets
Cryptocurrency
& Digital Assets Web3
Web3 Metaverse & NFTs
Metaverse & NFTs
