
- Mat Dave
- September 07, 2023
Understanding Blockchain
This article explains what a blockchain is, what components make the blockchain and also explores the concepts that help understand the technology better.
- Blockchain is a technology that enables the storage of data in blocks in a decentralized Ledger/database. It differs from traditional databases, where clients access data stored in one location. Whereas in blockchain the data gets duplicated in multiple computers or nodes that form the blockchain network.
- Blockchain is a distributed, decentralized ledger running on computer nodes over the network. Decentralized because all the nodes in the blockchain network equally share the software, data and all nodes have complete autonomy to read and write transactions to the blockchain.
- A transaction on a blockchain is anything that results in a change of state. For example, if A sends B 5 dollars, that is a transaction. One such transaction in blockchain could lead to multiple other transactions. Each transaction committed to the blockchain has to be verified and be valid.
- The interconnected blocks make the blockchain. A block has the header and the hashes of the transactions, stored as Markle root. The blockchain ledger is a table of entries with key/values mapping to the transactions. In the blockchain, a ledger exists in every node that is connected to the network.
- A transaction once committed is immutable (does not change).
- One of the goals of blockchain is to remove the middleman that exists in the traditional model. In the traditional model, the middleman could charge a fee or act in favour of some parties. Blockchain strives to reduce dependency on a middleman and replaces the arbitration provided by a middleman with a complex computational algorithm.
- The blockchain stores and tracks digital assets. Bitcoin and Ethereum are examples of cryptocurrencies using blockchain.
- The blockchain is analogous to a book, where the blocks are like pages in the book. A page number tracks the pages in a book, likewise, a unique nonce along with other header values represents the blocks. The transactions on a block are like the entries that make the pages in the book. Losing a page in a book will cause the pages to fall out of sequence, similarly tampering with a block will cause the blocks to fall out of sync.
- Nodes in the blockchain connect using the Peer-to-Peer network and interactions happen through the IPFS (Interplanetary File systems protocol).
- Bitcoin is the first decentralized cryptocurrency to use blockchain to store digital transactions. Bitcoin was found by a group of persons or pseudonyms person called Satoshi Nakamoto.
What is a block in the Blockchain – Block Concepts
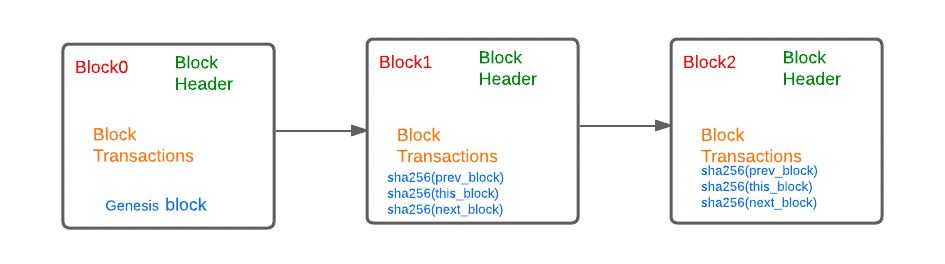
- A block is a storage bucket to hold the transactions made by a single user. A block will contain a block header, a block body. The Genesis Block is the start block in the blockchain.
- The blocks in a blockchain are linked using the hash of the previous block and the hash of the next block. The hash of the previous block is represented by the header SHA256(prev_block) and the hash of the next block is represented by the header SHA256(next_block).
- The header of a block consists of the following attributes:
- The transaction of the block, represented by the Markle root
- Nonce (complex unique value calculated by the miners)
- Timestamp
- The Difficulty information
- Transaction count ( how many transactions has happened in the block)
- The hash of a block is calculated using only the block header. The block header has the Markle root, which is the hash of all the transactions in the block. Building the hash with all the transactions is computationally complex as the transaction grows, the use of just the block header to calculate the hash provides better performance. A simplified representation of blocks is shown in the figure.
Genesis block
The first block in the blockchain is the Genesis block, and subsequent blocks are built on the data that was created using the first block. The genesis block is also called Block0. Genesis block starts with some initial header settings. A few values the Genesis block is initialized are the Markle root, block version, block time and the nonce.
Complexity Nonce
- The nonce is a unique random number, and it starts with multiple zeros that are required to be calculated by the miners in the blockchain before submitting a valid block. Calculating the nonce is key to verifying transactions committed to the blockchain.
- The nonce is a very large number, to calculate the nonce value is computationally very intensive. The nonce value is represented by 2 to the power of 68, which is initialized with a lot of leading zeros, which is a significantly larger value. The calculated nonce should be unique and less than the previous nonce values. As the blockchain grows, the complexity of calculating the nonce increases. Once the nonce is calculated, it is validated by all the actors of the nodes before it is submitted to the blockchain.
Consensus Algorithm – POW, POS
- Proof of Work (POW) is the consensus algorithm used by Bitcoin or Ethereum cryptocurrency as the rule of validity of a transaction before submitting a transaction to the blockchain. The miners using the proof of work in the blockchain, attempt to solve the complex nonce. Proof of work follows the longest chain rule, to validate a block. The success of solving the nonce depends on the computational resource (GPU’s) available with a miner/node.
- The POW uses a lot of computational power to calculate the unique nonce and this requirement of power increases as the blockchain complexity grows.
- To offset the high energy requirement by POW, there is another algorithm underway that is the POS (proof of stake). Proof of stake consensus algorithm is based on the amount of stake the user or a miner has in the blockchain, which the user can stake to be a full node or a validator node in the blockchain.
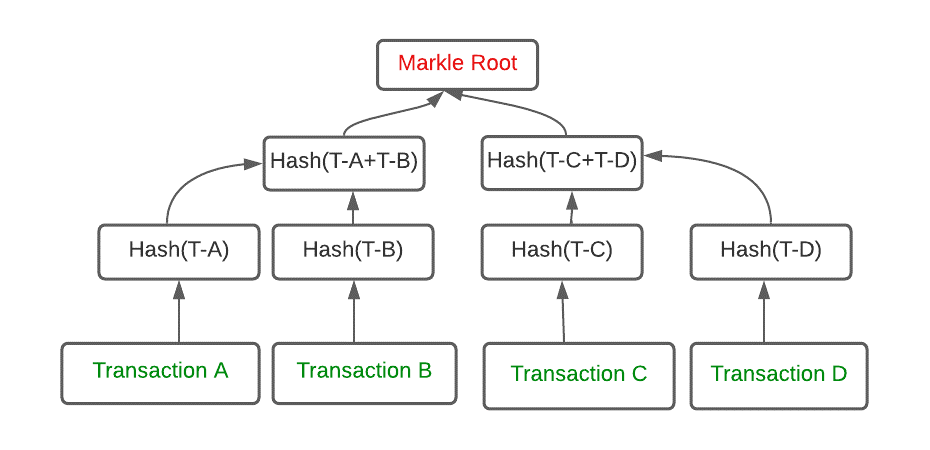
Markle root
- Markle root is the final hash value of all the hashes of the individual transactions in the block. Markle root is a binary tree, each transaction forms the leaf of the binary tree.
- Blockchain does not store transactions as plain text, the algorithm calculates the hash and stores only the hash of all the transactions in a block. The transactions in a block are divided into groups before the hash gets calculated. The Markle root will be the final hash of transactions. Below is the pictorial representation of the Markle Root. Changing a single transaction value will change the hash. This will cause a rippling impact on the following blocks.
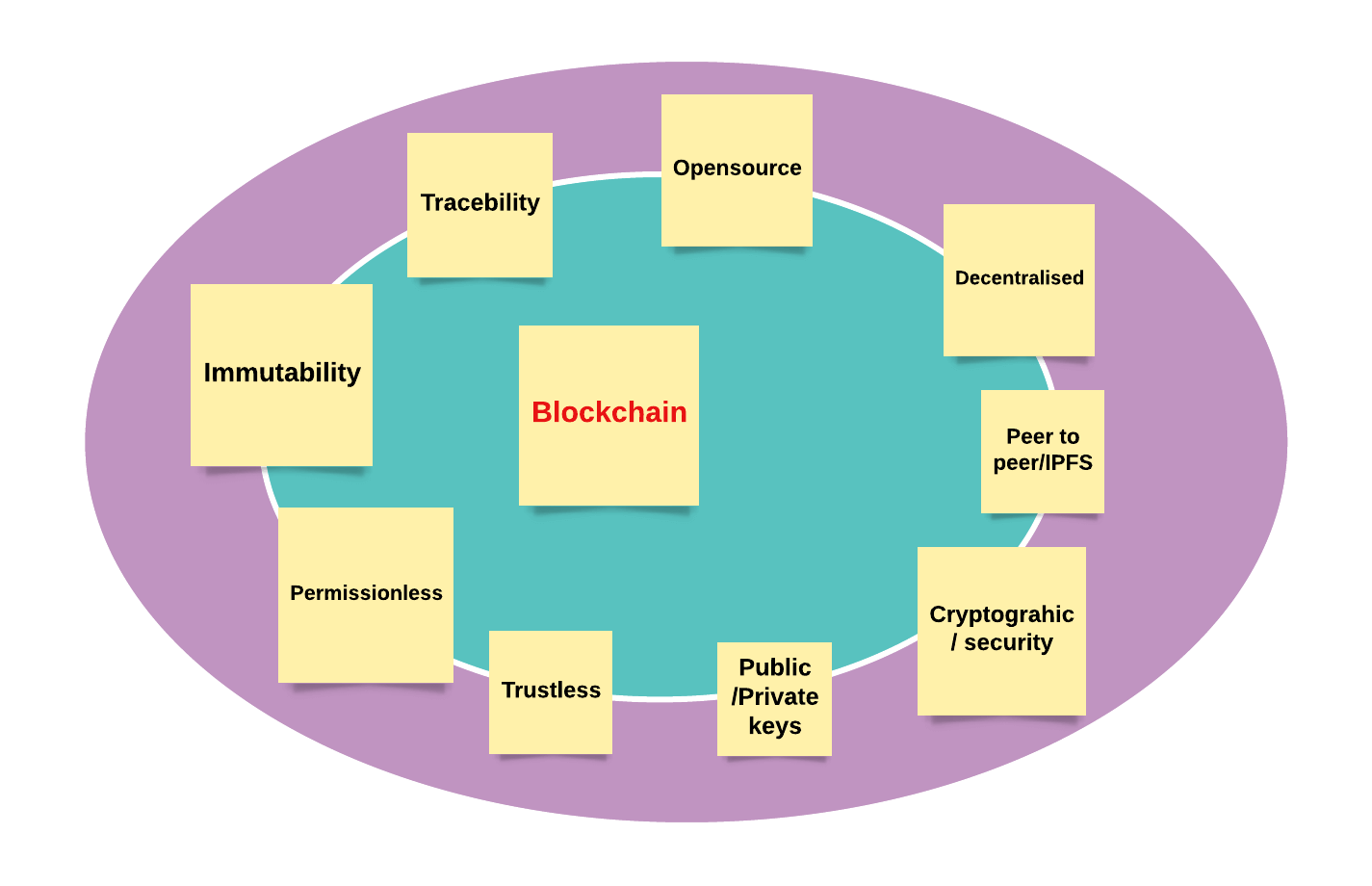
Features of BlockChain
- Blockchain is trustless. What does that mean, – instead of trusting humans or any organization manned by humans to execute and validate a transaction on the blockchain, it uses a complex cryptographic algorithm to hash the transaction and the exchange of messages happens through the signed asymmetric keys (private and public keys).
- Smart Contracts -Smart contracts are a pre-written set of instructions in a compatible programming language to satisfy an agreement. The transaction is complete and committed once the smart contract executes successfully. Smart contracts use the if-then-else statements to embed some logic or conditions to satisfy an agreement.
- The different smart contracts used by blockchains use programming languages like Ethereum (solidity), Cardano (Haskell) and python. Ethereum, Hyperledger fabric, Solana, Cardano, Multichain, Chia Blockchain and Quorum to name a few different blockchains available in the market.
- Blockchains can be public or private blockchains. Businesses can build a private blockchain, depending on the use cases.
- Availability, robustness, trusting a transaction, decentralization, consensus algorithm are all core features of the blockchain.
- What is the Longest chain rule consensus algorithm:
- In a public blockchain, multiple miners could mine the same block. This leads to duplicate blocks with the same transaction but the signature and timestamp will be different. Here, the miner will start working on the last block that was mined, and ignore the block he was working on. This block, when validated, forms the longest chain block. The algorithm will drop the shorter chain.
Decentralized
Decentralization is the core principle of blockchain technology. The goal of decentralization is to build a system that is not controlled by a group or a business or a corporate. In a decentralized network, a network of computers/nodes shares the data (ledger) and the processing power between them. This kind of setup is possible because of the computing resources available to the general consumer who has some technical background, and who will put the resources to use. Whereas in the centralized network, a single server or a small group of servers in highly available architecture provides the backend service or renders the data. Centralized network architecture is based on a request/response or a client-server model. The disadvantage of this model, if one or all the servers go down, then service will not be available.
Blockchain features
In a decentralized model, the services that fail are nearly impossible. However, the growth of decentralized networks requires more computational power and complex algorithms to allow trustless/permission-less models.
Peer-to-Peer Network
Nodes in a blockchain are connected through a peer-to-peer network. All the nodes share software and workloads and have equal privileges. The participants in the peer-to-peer network are full nodes or validator nodes. The nodes talk to each other using the Interplanetary File system (IPFS) protocol. Each node has a copy of the full blockchain ledger, in its local storage.
Interplanetary File system (IPFS)
In the peer-to-peer network, the nodes talk to each other through the IPFS protocol. Juan Benet, who is also the founder of Protocol Labs, created IPFS. The IPFS protocol has the following functional components.
- Naming, Identities, Files, Objects, Routing, Exchange, Networks
Let’s see a few differences between the IPFS and the HTTP protocol
- Difference between IPFS & HTTP :
- The HTTP is based on a request/response data transfer protocol.
- The IPFS is a file-based protocol system, address based on hashed value represents the contents. In the content-based address system, DHT stores the contents using computational Hashes. The set of computational hash tables is called a Markle Directed Acyclic Graphs (DAGs)
- A Markle DAG is a table in which the value of the identifier is the hash (SHA256) of the contents it represents. Using Distributed Hash Table and Markle DAG gives the performance of the IPFS.
Security through cryptographic algorithms
To calculate the hashes of transactions in the blockchain, different hash algorithms are used. A few of them are SHA256, SCRYPT and Elliptical Curve algorithms. For bitcoin mining, verifying a transaction before committing it to the blockchain requires a lot of GPU power.
Private and public keys
The public keys and private keys are used to sign and verify transactions in the blockchain. Cryptographic algorithms use the private key of the sender to sign the transaction. The receiver uses the public key, which matches the private key of the sender, to verify the transaction.
A digital wallet is an online address that can receive and send digital currencies. The public and private keys are the centers of successful transmission of the transactions between wallets.
Using public and private keys in the cryptographic algorithms makes blockchain more secure. A private key remains with the sender and not shared. The receiver to decrypt the message uses the public key.
Asymmetric or Symmetric-key Cryptography
- Symmetric key cryptography uses shared keys. This method is faster compared to Asymmetric keys. The keys in symmetric keys are the same as the public key.
- Asymmetric key cryptography uses public & private keys. This is more secure compared to Symmetric key cryptography. In asymmetric cryptography, the private key remains with the sender, the receiver gets the public key. We can generate the public key from the private key, but we cannot generate the private key from the public key.
- SHA1 (1024) and SHA2 /SHA256 (2048) are examples of private and public-key cryptography. Other cryptographic algorithms are ECC -> elliptic curve cryptography (ECC) & RIPEMD 160.
Trustless
Any nodes can join the blockchain network without proof of identity, this is possible because of the high degree of secure algorithms used to compute the transaction and verify a block. Changes to the transaction by a misguided node will be transparent and tracked.
Permissionless
To join the blockchain network, you don’t need specific permission. Blockchain supports the decentralized setup. Public blockchains require you to download/configure the software, connect to the network of nodes (Peer-to-Peer) and start working as a miner node or a validator node.
Immutability
Immutability means not capable of change. The immutability of the transactions in the blockchain is because of the complexity involved in modifying a block or changing the content in a blockchain ledger. Once the miners have verified the transaction and submitted the unique block to the blockchain, changing it is close to impossible. The modification of any transaction will change the hash of all the related blocks, which will cause a rippling effect on all the remaining blocks and such an operation is computationally not possible in the blockchain network.
Open source
The blockchain code is open source and is available to the developers to download, change and enhance. The open source model helps in developing Dapp’s (decentralized applications). Being open source promotes an open culture with no Government or organization control over the use of blockchain technology. One such example is the Ethereum blockchain code base, Ethereum Geth (Go-Ethereum).
Traceability
We can trace every transaction in the blockchain to its origin. A miner verifies the transaction in the network before submitting the block (transactions), to a blockchain. Any changes to a block will affect all the other blocks. The algorithms like SHA256 or SCRYPT are used to calculate the hash of the transaction. If we can trace one block (successful transaction), it will be easy to trace the previous block and the next block in the blockchain because the blocks are interconnected through the hashed link of header values to the previous and next block.
Globally decentralized ledger
The blocks written to the blockchain are tracked as a key/ value pair of submitted transactions which is stored in a ledger. This ledger is copied to all the local persistent stores of each node that participates in the P2P blockchain network.
Smart Contracts
A Smart Contract is a pre-written set of instructions in a specific programming language to satisfy an agreement or match a business use case in a blockchain. Once the smart contract is developed, it is converted to byte code and run on a virtual machine in the blockchain. Once it is executed successfully in the testnet blockchain, the developer submits the smart contract to the blockchain. These contracts will be in the blockchain and can be reused to carry out pre-programmed instructions to fulfill a contract.
The difference between a traditional contract system and smart contracts is that, in traditional systems, lawyers or legal professionals write smart contracts and those are fulfilled by working with the end-users, whereas smart contracts are written using programming languages and have a set of if-else- then statements, that are coded to satisfy an agreement.
The programming languages that support writing smart contracts are solidity (Ethereum), Cardano (Haskell), etc.
Public Blockchain vs Private Blockchain
A public blockchain is open to anyone with computational resources to join the blockchain and has a more complex consensus algorithm to verify each block or before reaching a consensus. The computational power required to calculate the unique nonce is very large in the public blockchain. Public or private blockchain uses smart contracts to fulfill a contractual agreement.
A private blockchain is not open for everyone to join, a nominated administrator, who acts as an arbitrator, controls the registration. In the private blockchain, when there is a conflict, the arbitrator who decides the last block to be worked on resolves it. The private blockchain is less expensive to maintain and the consensus algorithm is less complex.
To successfully run a private blockchain, a legal contract will need to be signed and agreed upon. The public, compared to a private blockchain, has different requirements for data access and privileges. In the private blockchain, the blockchain administrators are given privileges to grant and revoke access to a particular node. Miners in the blockchain are given executable privilege to validate and write a valid block to the blockchain. Certain actions require only read privileges, which allows for reading data from the blockchain.
- SUMMARY
Blockchain is a decentralized, immutable transaction store of blocks on the global network. The interaction between the nodes in the blockchain is through a peer-to-peer model. The transactions on the blockchain are immutable (non-changeable), this is possible because of the crypto algorithms used to calculate the hash of all transactions and blockchain stores this hash in a ledger. Any changes to the value of the transaction will change the Hash.
The nonce, which is a computationally difficult value, is the numerical value that is 2 to the power of 68, and this value is unique for a block. Trustless and permission-less are some other characteristics of blockchain technology.
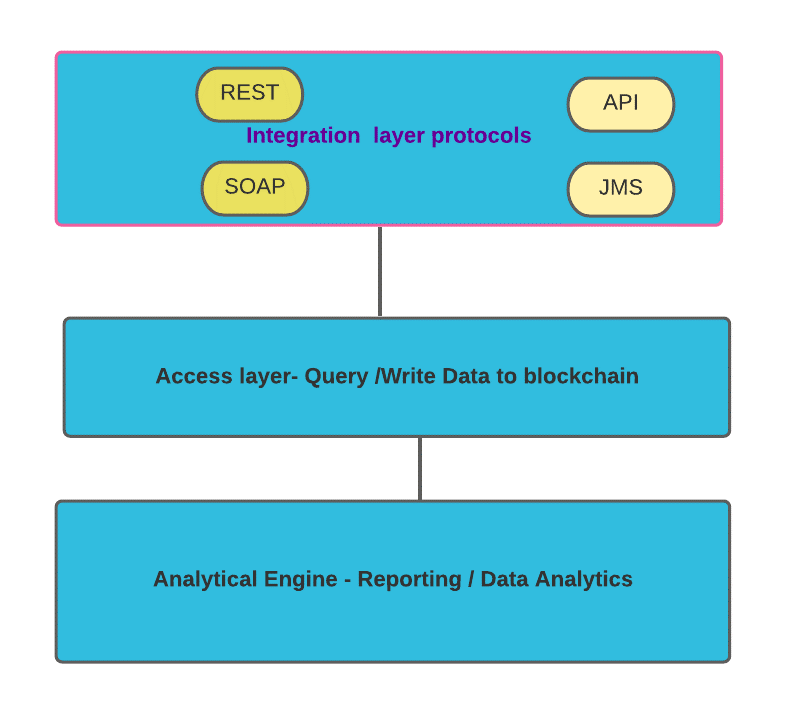
Blockchain Architecture (Simplified)
Different layers make the blockchain architecture accessible to the nodes and allow nodes to manipulate the data on the blockchain. The layers are :
- An Integration layer,
- Blockchain Access layer &
- An Analytical layer.
The integration layer is used to interact with the blockchain layer. The integration layer comprises REST API, SOAP, Java Messaging Services protocols and other core functions like Identity Management, Governance and Data intelligence.
The blockchain layer provides functions to access blockchain data and write data & also to execute query transactions. Applications access the core functions of the blockchain through the blockchain layer.
The Analytical layer provides reporting and dashboard features.

































































 Guides
Guides News
News Blockchain
Blockchain Cryptocurrency
& Digital Assets
Cryptocurrency
& Digital Assets Web3
Web3 Metaverse & NFTs
Metaverse & NFTs
