
- Prerana Kulkarni
- September 12, 2022
What is Byzantine Generals’ Problem?
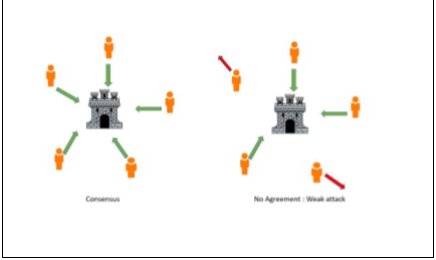
A Byzantine fault or Byzantine General’s Problem is a condition typically seen in a (specifically distributed ) computer system, where one or more components fail and exhibit inconsistent behavior by sending conflicting information to the different parts of the system. A Byzantine generals’ problem also abstractly describes coping mechanisms for these types of failure. Consider a fortress surrounded by Byzantine generals. They are geographically separated and can communicate only through messages. They can either retreat or attack. The important thing
is that all the generals should agree on one common decision: attack or retreat. Any tepid attack by a few generals would worsen the situation than either co-ordinated attack or co-ordinated retreat. The complexity increases as there are traitors who would do their best to stop generals from reaching an agreement.
There are two solutions to resolve this problem
For every t no. of traitors, there should be more than 3t+1 generals in the system. The messages communicated should be secured, i.e., unforgeable and signed. With this, any number of generals could cope up with an arbitrary number of traitors.
How Blockchain is BFT (Byzantine Fault Tolerant)?
In a traditional finance/banking system, only a centralized authority can record the transactions and update the balance, thus preventing double-spending. Double-spending means spending the same amount twice; it could be accidental or malicious. Bitcoin, the first use case of Blockchain technology, is a peer-to-peer digital cash system having a network of trustless nodes (peers) with no central authority. In a peer-to-peer system, without centralized authority, preventing Double-spending attacks or other malicious attempts to tamper with the transactions or balances can be challenging.
Bitcoin prevents these types of attacks with asymmetric cryptography and a consensus algorithm, Proof-Of-Work (POW).
Asymmetric Cryptography
Every transaction is cryptographically signed using public-private key pair and is verified by the nodes. Hashing algorithms, the Merkel tree, and the way each block would have the previous block hash make the blocks tamperproof, so the traitors cannot break in.
Proof-Of-Work
The nodes must race to solve a complex mathematical puzzle with varying difficulties. Only the node that solves it first gets to add the new block to the blockchain and receives reward & transaction fees. All other nodes agree and update their local copies accordingly. POW ensures that if the traitors or malicious nodes attempt to alter any block or perform double spending, they would have to solve the complex mathematical puzzle and build every block that comes after that particular block in the blockchain, which will be very expensive and practically infeasible. Also, to force any invalid block in the blockchain, one needs to own more than fifty percent of computing nodes, which is an unachievable task, given there are thousands of nodes in the network.
Proof-Of-Stake
POS is another consensus algorithm used, where a validator is selected based on the proportion of tokens it’s staking, i.e., the more the stakes higher is the chance of getting picked as a validator. A validator is a node that can add a new block to the blockchain; it needs to commit the tokens for a certain period to the network, the process known as staking. Validators act in good faith as they are staking their tokens; also, they receive block rewards on a successful addition of the block. Cardano, Cosmos, Polkadot, and Solana are among many popular cryptocurrencies that use the POS consensus mechanism; Ethereum 2.0 will also use POS.




































































 Guides
Guides News
News Blockchain
Blockchain Cryptocurrency
& Digital Assets
Cryptocurrency
& Digital Assets Web3
Web3 Metaverse & NFTs
Metaverse & NFTs
