
- Shikhil Sharma
- August 16, 2022
In recent years, the multitude and adoption of Blockchain technology have risen enormously in the banking and manufacturing industry. Its decentralized nature, transparency, immutability and automation are powering companies and organizations worldwide to create innovative applications and build sustainable environments for social and economic structures.
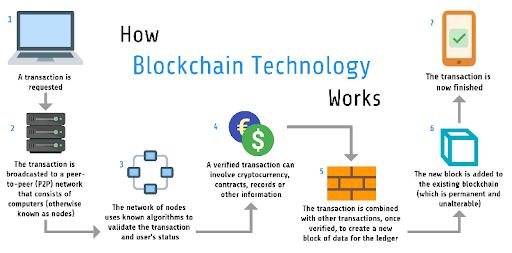
How blockchain technology works; Image courtesy: Medium
According to recent research by IDC, worldwide spending on blockchain solutions is forecast to be $4.1 billion in 2020, an increase of more than 50% compared to 2019.
The main purpose of Blockchain technology is to provide transparency, data integrity, transactional speed and security to integrated applications, but it doesn’t necessarily guarantee the immunity from cyber attacks in a world hacking scenario.
Companies and organizations using blockchain for financial and manufacturing use cases are facing more targeted cyberattacks on their applications infrastructure which is leading to either their business disruption or huge money losses. Did you know 2019 was the year that saw more crypto hacks than any other year in the history of the cryptocurrency industry? Yes, there was a loss of more than $4 billion during the last year for crypto transactions.
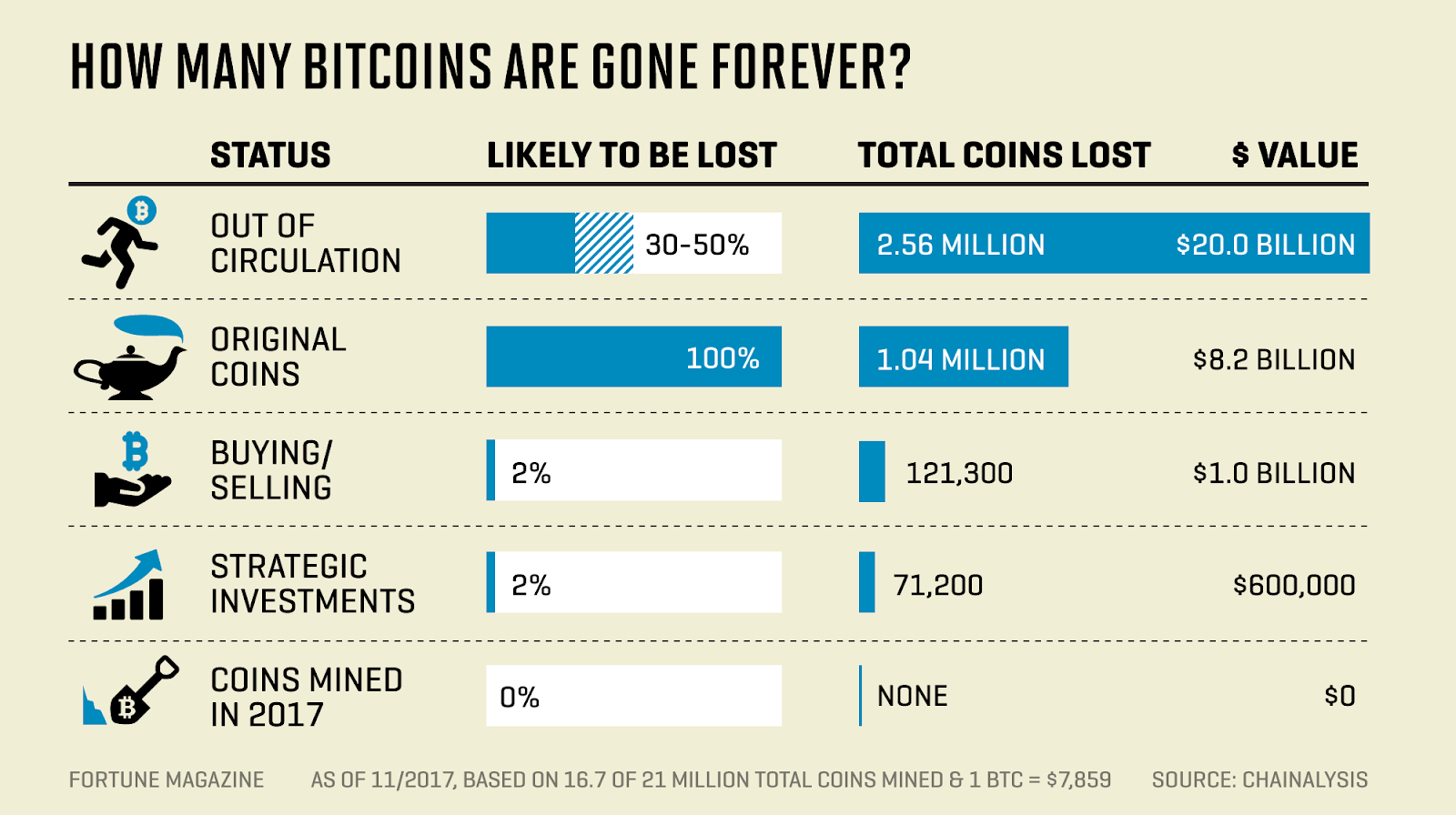
Source: Fortune
According to an article in Fortune magazine, more than 4 million bitcoins are missing. This number accounts for 17% to 23% of the total cryptocurrency, which worth more than $8,500 each.
In this article, we will discuss more on Blockchain security and how it is a need for today’s online businesses that have implemented this for building their applications.
What is Blockchain Security?
As the name suggests, Blockchain is a chain of ‘blocks’ that contains information or records about transactions. Each block links to two other blocks on either side in order to form a chain. It is the complexity of the Blockchain technology which makes it almost impossible for hackers to tamper with. Because then a hacker will have to alter other records linked with the block as well in order to avoid detection.
Apart from this, blockchain has some other inherent properties that can provide additional security. Some of the properties of Blockchain technology are:
1. Increased Capacity
It is one of the most important security benefits provided by blockchain technology. Here, the structure of the linked system of blockchain is more than capable of increasing the capacity of an entire network. The reason behind this is that all the systems working together offer greater power than a handful of devices working separately.
A project by Stanford University to create a supercomputer that simulates the folding of protein for medical research is a perfect example of the increased capacity benefit of using blockchain technology.
2. Immutability
Immutability is also one of the crucial features that blockchain technology can offer. It means that once a transaction is done, it is impossible to erase it from the database, i.e; the distributed ledger remains unaltered.
3. Faster Settlements
If you have a bank account, you must be aware of the fact that banking transactions take time. Blockchain does not have a problem with that, as it can make relatively the financial transactions very swift for users. This can save a lot of time and can provide convenience to the customers.
4. Encryption
Blockchain uses two types of cryptography algorithm to maintain data authenticity and protect it from foul play, which are — Asymmetric-key algorithm and Hash function encryption. In the asymmetric-key encryption, there are two keys involved – encryption key and decryption key, whereas, in the hash functions encryption, there are no keys just hash functions, which works only one-way. This is to say, if encrypted with the hash algorithm, no encrypted data could be reversed to its original plaintext in a blockchain. This protects blockchain from tampering and holds data integrity.
5. Decentralization
Another key facet of Blockchain technology is its decentralized and distributed mechanism. No central authority enjoys autonomy over the maintenance of a blockchain. Instead, data is added piece by piece in a collaborative manner by the participants in the blockchain. Moving the power away from a central conglomerate boosts expansion, coordination, diversification and promptness. Hence, each user on the network will be equipped with the latest data almost instantaneously.
Security issues with Blockchain applications
Besides having its own security capabilities, applications that are built using Blockchain technology are still vulnerable to a wide range of cyberattacks. Vulnerabilities in blockchain applications are the primary target for hackers. But the complexity and pace of modern application development make effective detection and remediation of these security issues increasingly difficult.
Here are some of the targeted attacks that happened on blockchain-based applications:
‘51% Attacks’
If a blockchain miner or a group gains access to more than 50% of the network, it will make it easier for them to control and manipulate the system. This attack has been dubbed as a ‘51% attack.’ They will be able to add new transactions without any real deposits. The most ‘51% attacks’ occurred in 2018 on some of the famous cryptocurrencies such as Verge, ZenCash, Ethereum Classic, etc. For the prevention of 51% attacks, one must be vigilant of minings and should use a higher hash rate.
Phishing
Phishing is one of the most common hacking techniques. It can mimic the emails from trusted and reputed sources. These emails are sent to the owners of digital wallets, asking them to fill their personal information on the fake links. As per a report of Chainalysis, more than $225 million were lost to phishing scams in the first of 2017.
Sybil Attacks
Sybil attacks involve the use of multiple fake identities. In other words, a single party can run a number of nodes at the same time, using fake identities to disrupt the activities of the network by crashing it.
Routing Attack
The information of blockchains can be intercepted by hackers by compromising ISPs. The compromised Internet Service Providers can also be the cause of this type of attack.
Direct Denial of Service
DDoS attacks are also a major security issue for blockchain applications. In this attack, hackers flood the network with false requests consequently increasing the traffic of the network and disrupting legitimate requests or they target applications with the low and slow attacks to make these applications unavailable for its users
How to strengthen the Blockchain security for your application:
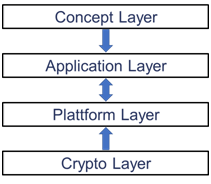
A typical blockchain system is developed with a layered approach (as shown in the below figure) mainly focusing on its security aspects.
Layer Architecture of a Blockchain System, Image courtesy: Medium
The above 4-layered approach shows that the security problems can arise at each level i.e. at the concept layer, application layer, platform layer, and crypto layer. In this article, we’ll talk about how to strengthen your blockchain security at the application layer during your application development life cycle.
Performing comprehensive testing and combining multiple analysis techniques to test any application, service, or containers will help in strengthening your blockchain application. Here are some guidelines that you can follow to test your Blockchain application and secure it from the cyberattacks, data breaches and vulnerability exploits:
- Performing Static Analysis testing (SAST) to identify security loopholes in the proprietary code of the application.
- Performing Dynamic Analysis testing (DAST) to test for security vulnerabilities in applications in the production environment.
- Performing Interactive Application analysis/testing (IAST) to thoroughly test for hidden inputs, hidden files, and configuration information, etc. in an application running in real-time, in the development process, QA, or in production.
- Performing Software Composition Analysis (SCA) to check for any vulnerable outdated libraries, open-source components, and containers used in the development. You can use this OWASP dependency-check tool to do this.
- Performing a detailed penetration testing for your Blockchain-based application to test and discover security loopholes and vulnerability exploits using the hacker approach. You can do this by using a variety of open-source tools that are available on the Internet.
Get Professional Help…
Following the above security measures will help you strengthen the security of your blockchain system and applications, but nothing beats professional help. Astra Security provides complete Blockchain Security assessment and penetration testing for the applications that are built on this technology at a very nominal price. Or learn how it’s done with this article on blockchain security audit/assessment by Astra.



































































 Guides
Guides News
News Blockchain
Blockchain Cryptocurrency
& Digital Assets
Cryptocurrency
& Digital Assets Web3
Web3 Metaverse & NFTs
Metaverse & NFTs
