- Ayushi Abrol
- February 21, 2022

In response to the growing usage of digital assets within businesses, companies want secure and efficient solutions to scale and operate effectively. For a successful security program, selecting an ideal approach is important to ensuring desired security levels. A prominent aspect of the crypto world is now comparing multi-signature and multi-processing.
Some believe Multiparty Computation is more secure than Multi-Signature wallets, while others consider multi-signature wallets the safer option. So, how do you make a decision?
The only way to figure out the better option is to compare the two. The following discussion takes an in-depth look into Multiparty Computation and multi-signature wallets and their differences in great detail.
The two most common options in terms of technology for protecting private keys are Multi-Signature and Master Password Encryption (MPC). A basic understanding of the technologies is necessary before highlighting the differences between Multi-Sig and MPC.
Understanding Multi-Sig
Multi-Signature refers to a digital signature process that enables multiple users to sign a single transaction on behalf of the group. Each Multi-Signature address is often associated with several private keys. When Bitcoin introduced an alternative to single key addresses in 2012, Multi-Signature addresses surged to the forefront.
In the same period, another type of address called Pay-To-Script-Hash (P2SH) became clear. Furthermore, the P2SH process required consistency, with identification attainable by ensuring that they begin with a ‘3’ rather than a ‘1’. When it comes to P2SH addresses, the most interesting feature is the ability to enforce transactions with multiple private keys.
The most common way for storing digital assets was to use a single private key before Multi-Sig wallets were developed. Digital assets associated with a specific key can be accessed by persons who possess the private key. Through multi-signature wallets, an additional layer of security has been introduced by requiring signatures from multiple keys.
The Multi-Signature wallet approach appears to offer reliable solutions to many of the problems associated with single-signature wallets. In addition, Multi-Sig wallets have a drawback in the form of protocol dependency. In order to understand Multi-Party Computation (MPC) and Multi-Signature, you must understand why it was introduced.
Multi-Signature Failure: Where Did it Come From?
Some crypto protocols do not work well with Multi-Signature. Consequently, Multi-Signature wallet providers experience many difficulties with supporting new chains. In order to implement the on-chain multi-signature solution, wallet providers need to implement different codes. Failed multi-signature implementations, on the other hand, could cause major problems. As an example, a $30 million Ethereum wallet was hacked because an inappropriate implementation of the Multi-Sig Parity wallet was used. One of the Parity Wallets was also hacked, causing almost $300,000 in lost digital assets for some users.
In addition, multi-signature approaches could not provide the desired operational flexibility for enabling an organization’s growth. The methods by which users access and transfer digital assets must evolve as an enterprise grows. One possibility would be to change the number of employees required for signing a transaction. As well as adding new key shares with the addition of new employees, revoking key shares with the departure of employees can be another scenario. There are significant drawbacks associated with multi-signature addresses in these scenarios.
Understanding MPC (Multiparty Computation)
Private key security is one of the prominent challenges that exist today. There was a need for Multiparty Computation as a possible solution to address this problem. The idea of a single private key disappears due to Multiparty Computation because it doesn’t involve collecting a single private key in its entirety. At the time you create the wallet or when you create your signature, you do not have a single private key. As a result, private keys are vulnerable to failure in a single point of failure due to Multiparty Computation. MPC uses the following procedures to ensure relief from the burden of a single point of failure.
The individual secrets for each endpoint are never shared among them since they are randomized.
Endpoints that participate in the protocol for constructing a decentralized wallet can compute the wallet address or public key associated with each group of individual private shares.
Whenever a blockchain transaction requires a signature, at least three endpoints (3 at a minimum) must participate in a distributed signature process. Validating the transaction and the policy separately, followed by signing it, is required at every endpoint.
In view of the fact that the private key never stays on any particular device at any specific time, MPC can provide an additional layer of protection for the private key. In addition, the distributed nature of multiparty Computation gives team members the capability to establish the need for multiple verifiers of transactions. Additionally, multiparty Computation offers the flexibility to update and maintain signature schemes on a regular basis.
Differences Between Multi-Signature And MPC
Understanding how Multiparty Computation and Multi-Signature techniques work can help you comprehend private key security. Certainly, you can find the answer to the question ‘Is Multi-Sig more secure?’ By considering the additional security layer that multiparty Computation provides. Compared with Multi-Signature and Multiparty Computation approaches, the security aspect is one of the most important benchmarks. However, numerous other aspects can be compared. Let’s examine some of them here.
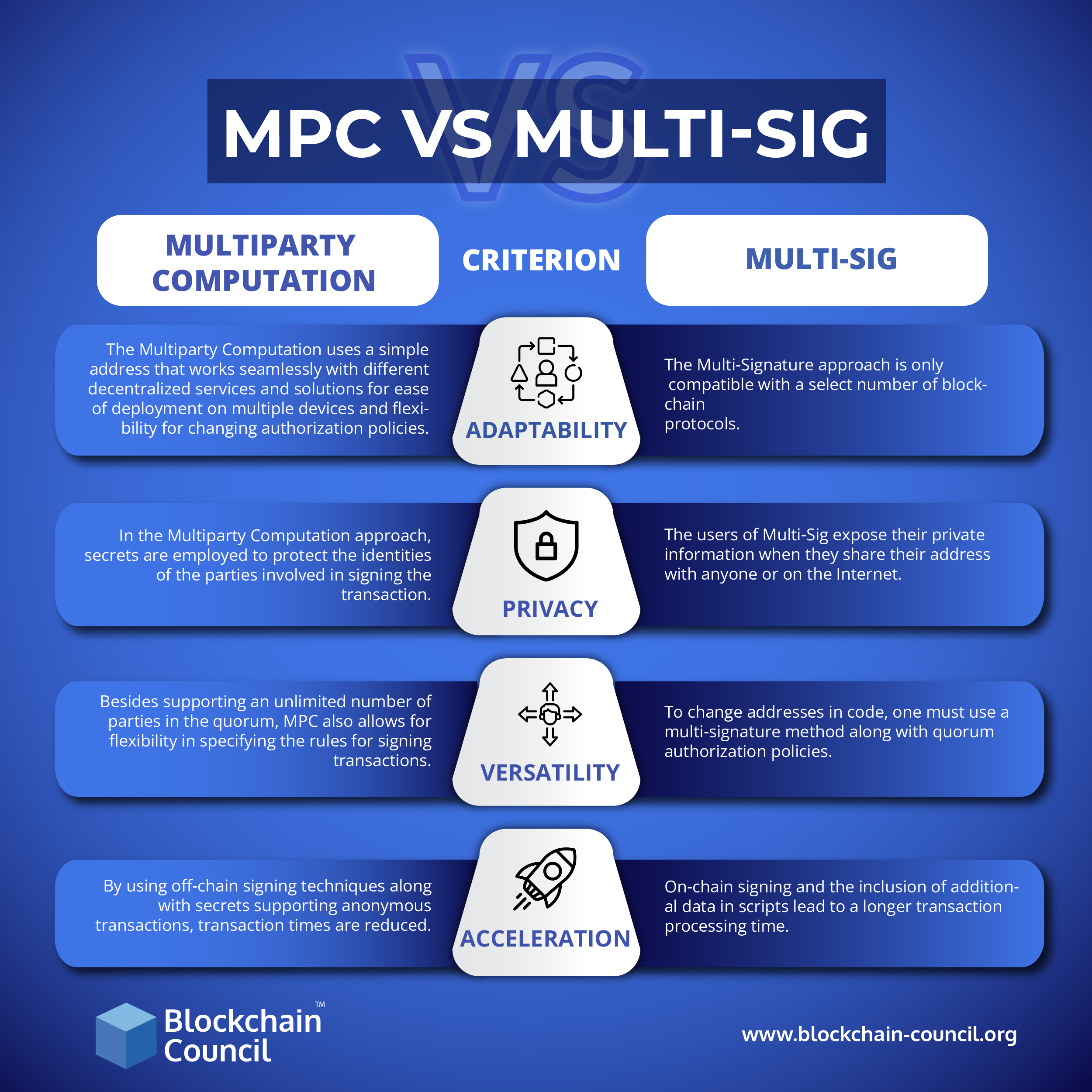
Adaptability
As a matter of fact, in a comparison of MPC and Multi-Sig, compatibility should be one of the most important aspects. The bad news about Multi-Signature is that it is only compatible with a limited number of blockchain protocols. A multiparty computation, in contrast, is completely independent of blockchains and can be used with almost any ledger. Furthermore, the Multi-Signature approach does not support decentralized apps or DeFi services adequately. An MPC address, on the other hand, is simple and can be used with nearly any type of decentralized application, whether it be web or desktop.
Furthermore, multiparty Computation has the advantage of being easy to implement on a desktop, mobile, or server device, offering flexible policies for authorization. In that case, only blockchain addresses could be accessed by the hardware security module. The changes to the infrastructure would not have any impact on HSM operators. Multi-Signature wallets, however, can pose a problem for HSMs due to their inability to support blockchain protocols.
Privacy
Regarding the answer to the question, ‘What’s the difference between MPC and Multi-Sig,’ privacy is another crucial factor to consider. A Multi-Signature user can trace and identify transactions with their address and relate them to their identity if they share it with someone or on the internet.
Multiparty Computation, however, makes use of secret information in transaction signing. It is known that the secrets are visible to the participants, but they do not know who owns them. In this post, I’ll outline the processes in multiparty Computation, which will help you understand the implications of privacy.
- Notifications are sent to users regarding specific transactions
- Go through the multi-factor authentication process
- Examine the transaction carefully
- Validation or cancellation of the transaction must take place
Secrets in Multiparty Computations make it difficult to learn which ones are used for signing a specific transaction. Even though anonymity can be a significant hindrance to the mainstream adoption of MPC in corporate settings, it still offers a great deal of value.
Versatility
When the multiparty Computation is defined, the question of ‘Is Multi-Sig more secure’ never gets answered. Multiparty Computation adds an additional layer of security to private key cryptography by providing multiple verifiers for signing transactions. Nonetheless, do multiparty computations provide the desired flexibility? Whenever an address is changed when using the multi-sign approach, the code must be modified.
Because of this, enterprises must take advantage of third-party IT services for everyday IT tasks alongside additional investment of time and money. Further, multi-sig also presents a problematic issue in that it restricts the ability to support quorum authorization policies. As a result, you can have an unlimited number of parties in the quorum. A transaction can be signed using any of the following rules: the amount of money, the type of payment, the geographic location, and any other factors you choose.
Acceleration
As you learn about multi-signature transactions, you will notice that they require on-chain signatures and confirmations. Therefore, multi-signature transactions are clearly on the downside when compared with multi-signature transactions based on speed. By using an off-chain approach for multiparty Computation, transaction speeds can be enhanced. In the case of multi-signature transactions, scripts have to include more data for including metadata regarding every signer.
In this way, the amount of time needed to process a new block increases, as does the final cost to the end-user. By contrast, users process their secrets independently using a multiparty computation approach, thereby ensuring that devices are always available. The anonymized transaction signing of secrets in multiparty Computation is supported. Moreover, the lack of data also guarantees a plausible diminution of transaction costs and time.
The following comparison table explains the differences between Multi-Signature and multiparty computations.
Let us see the tabular comparison between MPC And Multi-Sig
Do You Need Multi-Sig or MPC Protection for Your Crypto Assets?
Although threshold signing and Multi-Sig are aimed at addressing the same basic issue, threshold signing has many advantages over Multi-Sig.
Among the primary advantages of Multi-Sig is that it requires little cryptographic expertise to build and deploy. Nevertheless, threshold signatures are widely accepted today to be a far better option in enterprises where large amounts of money are at stake.
Impact on Cold Storage and High-Security Storage
In some cases, users of MPC claim that it does away with the need for “cold storage,” but that is not the case.
Wallets that make use of cold storage simply mean that the private key material is stored offline. Hot storage is a term that is used for wallets that keep the private key material online. Whether there is one private key or three, whether MPC is used or not, the need to secure private key material is exactly the same.
Hacking is a problem that continues to plague the industry. A breach occurred at Facebook. There has been a breach at Google. Hackers have repeatedly targeted the US Government. Online storage of MPC private key parts exposes them to the same hacking and theft risks as other online data.
Conclusion
As a final note, it is clear that Multiparty Computation clearly trumps Multi-Sig in the MPC vs. Multi-Sig debate. Multiparty Computation has the edge over multi-signature approaches primarily because of security when it comes to private key security. Multiparty Computation ensures that the private key is never stored in one place and removes the concept of a single private key as a whole entity.
Multiparty Computation is a refined method to replace the Multi-Signature approach because of its numerous benefits. You can benefit from Multiparty Computation in terms of efficiency, flexibility, compatibility, and speed. Nevertheless, it would be unreasonable to completely discount the use of Multi-Signature wallets.



































































 Guides
Guides News
News Blockchain
Blockchain Cryptocurrency
& Digital Assets
Cryptocurrency
& Digital Assets Web3
Web3 Metaverse & NFTs
Metaverse & NFTs
