
- Pradeep Aswal
- September 10, 2024
P2P Meaning & Definition
Have you ever wondered while playing online games, how do you connect with players around the globe so easily? The answer is: peer-to-peer networks. P2P networks have revolutionized the way we share and consume content online. From music to movies and even software, P2P networks have made it easier than ever to access and share large files over the internet. The term “P2P” stands for “peer-to-peer.” It refers to a network model where each participant, or “peer,” has equal capabilities and can initiate or complete transactions without requiring a central authority or server. In a P2P network, all peers share resources directly with each other, such as files, storage space, or processing power, making the network decentralized. This model is commonly used for file sharing, blockchain technology, and various applications that require direct, decentralized interaction between users.
But what exactly are P2P networks and how do they work? Despite their widespread use, the technicalities of P2P networks are often a mystery to many people. In this article, we will explore the basics of P2P networks and how they operate, giving you a clear understanding of this powerful technology. Let’s dive in!
What is a Peer to Peer (p2p) Network?
In the simplest terms, a peer-to-peer network is a network created whenever two or more devices (usually a computer) are connected and share resources. But what creates the main difference here is that a peer-to-peer network, unlike conventional network systems, forms an ecosystem where the computers are connected through a single server computer. It can also be seen as a network where multiple computer systems are connected through a single server that enables the transfer of files from one end to the other.
Moreover, a peer-to-peer network also serves the role of a permanent infrastructure that can connect more than a dozen computers in a small region amidst the conventional offline environment. In addition to this, if you want to learn more about peer-to-peer networks and how they can be beneficial in the field of Blockchain, you can go for a Blockchain certification course from any certified platform.
What is a P2P (Peer to Peer) Network architecture?
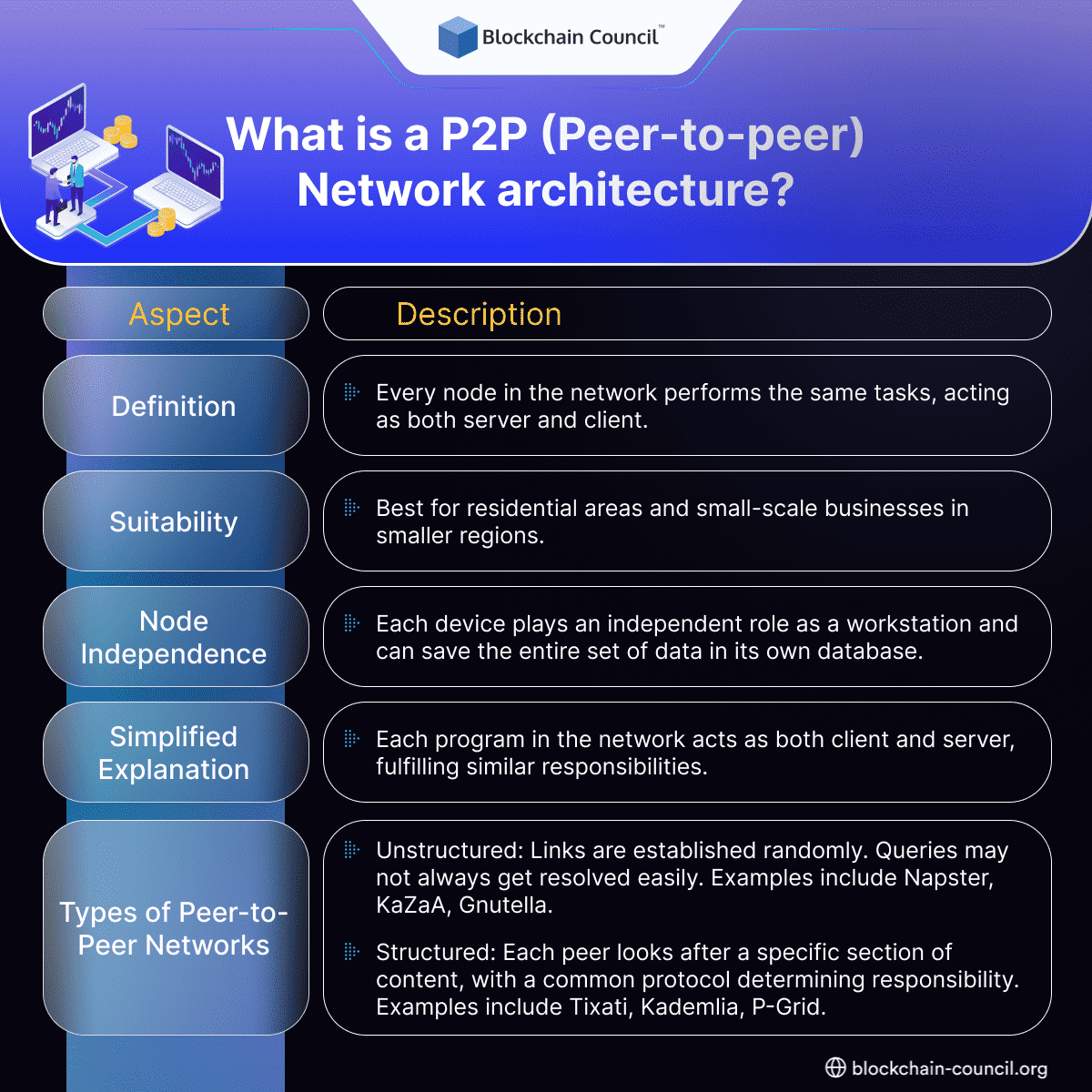
Peer-to-peer network architecture is a kind of network where there is absolutely no division of activities among various other sections. Every node performs the same task and set of actions where each device serves the purpose of both the server and the client. Response of network architecture established over the computer networking ecosystem under this model is such that each and every workstation is responsible for equal tasks but fewer devices are connected to the main server. The peer-to-peer network architecture is most suitable for residential areas and small-scale businesses in smaller regions. This is because in such networks every device plays an independent role as a workstation as it has access to save the entire set of data in its own database.
To state in layman’s language, the general peer-to-peer architecture is designed keeping in mind the functionalities of a single software program. In this way, every program is responsible to perform its task while fulfilling the role of both client and server carrying similar responsibilities and abilities. Moreover, if you wonder how to learn Blockchain basics, you can also get multiple content pieces to help you throughout the process.
Further, peer-to-peer networks can be classified into two major categories based on how the sections in the network are linked to each other. Here are the two major types –
- Unstructured networks: An unstructured peer-to-peer network is one where the links in the network are established randomly. Such networks are easy to construct as any new peer that would like to join and contribute to the network can do so by copying the existing links of another section and then forming and spreading its own links..
However, it is equally important to know that the queries may not always get a resolution in unstructured networks so there can be hassles. For instance, a popular piece of content may be available to certain peers but if any other is looking for content that is rarely available, then the user may not be able to search for it..
Examples – Napster, KaZaA, Gnutella, etc.
- Structured networks: Unlike unstructured networks, structured ones allow each peer to look after a specific section of the content over the network. These networks assign a specific value to each content and peer in the network which is then followed by a common protocol that determines which section is responsible for which part of the content. In this way, whenever someone reaches out to a peer to search for content, the network uses the common protocol to determine the section responsible for data transfer and direct the search query towards the peer responsible for it.
Examples – Tixati, Kademlia, P-Grid, etc.
How does a P2P network work?
Coming to the technical aspects of our topic, it is also necessary to understand the mechanism behind the working of peer-to-peer networks. While things are quite different in the case of Blockchain, where any Blockchain developer can resolve your query, the basic mechanism of a peer-to-peer network follows a different process. Generally, these networks have no distinct server for authenticating their users. Each device across the network manages its own security which makes it necessary to create a separate user account for each device that the user would need.
- Usually, a user stores their file on their own devices, which is a computer in an ideal situation. They are themselves responsible for ensuring that these files are properly backed up for data recovery. Furthermore, the devices usually run both server and client software in a peer-to-peer network and can also make the resources available to other users on the network.
- From the perspective of simplicity in network architecture, a peer-to-peer network is relatively simple to set up and is often an ideal deal for networks that require less than 10 devices and prefer a server-based solution over any other option.
Let us take an example to understand how a peer-to-peer network actually works. Suppose you want to download any file from the internet. The website you visit is like a store that has the file you want to download. The website plays the role of a server, which means it sends the file to your computer or device, which is the client. Just like driving on a one-way road, the data you download only flows in one direction, from the website to your computer. This is because the website is the only one that has the file you want, and your computer is the one that wants to receive it.
Similarly, in the case of a peer-to-peer network, whenever you browse the internet to search for a particular piece of content, this task of downloading is controlled in a slightly different manner. It is essential for you to have any peer-to-peer program installed on your device that can enable you to generate a virtual peer-to-peer network. Once this is established successfully, the file you want to download from the internet is received in the units of bits that come from different devices in the network that already have the same file on them.
At the same time, the file is also shifted from your device to other computer systems that call for it. This entire process works in two ways the files convert into small bits of data that come from your device. Once this process gets completed, the network releases your file after sending the request, which is then followed by the final transfer of the file to all connected peer devices.
Characteristics of P2P Network
Peer-to-peer (P2P) networks have become increasingly popular in recent years, especially for applications such as file sharing, instant messaging, and online gaming. P2P networking is a type of distributed networking architecture where computers communicate directly with each other, rather than through a centralized server or hub.
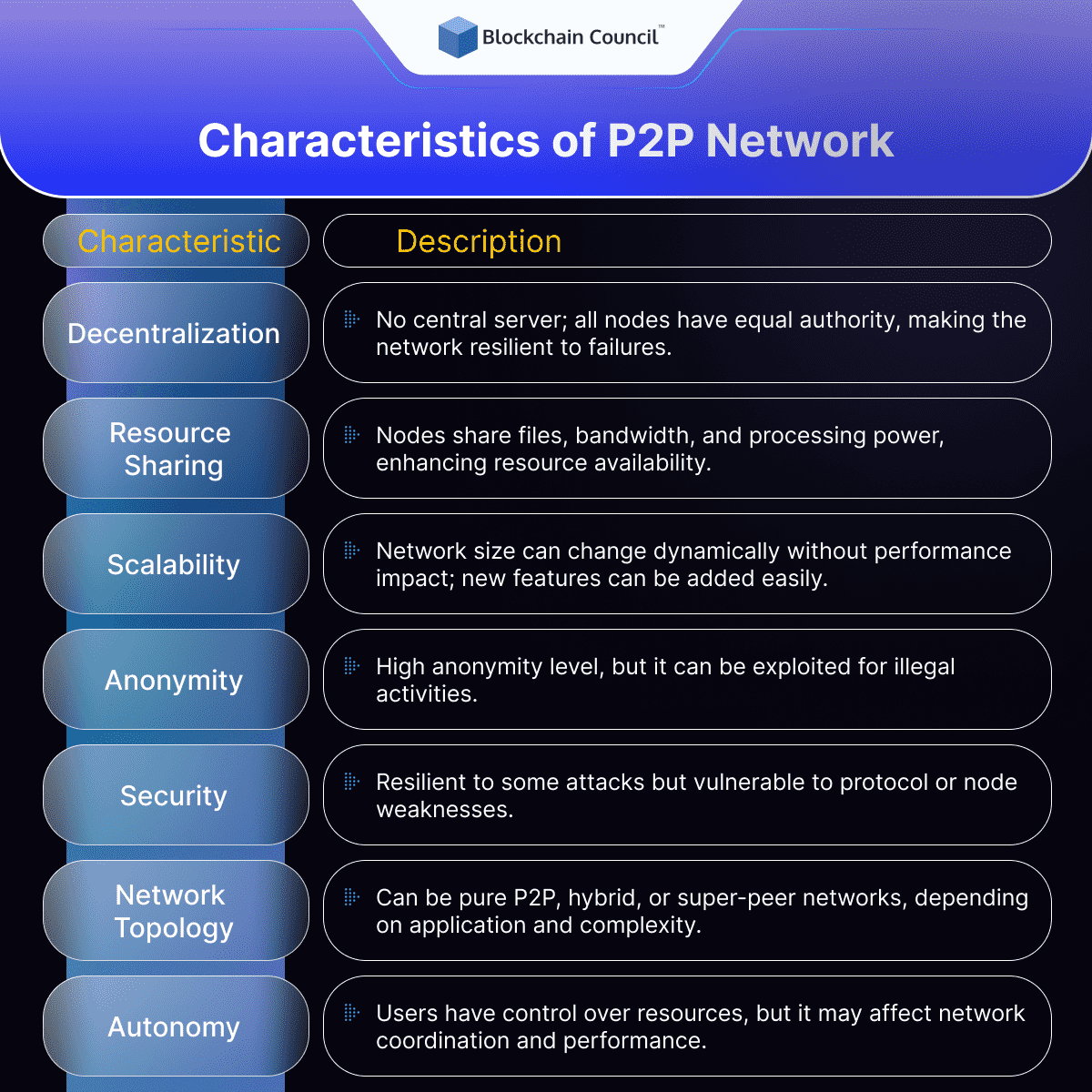
Decentralization
One of the defining characteristics of P2P networks is their decentralized nature. Unlike traditional client-server networks, where a central server manages all communication between clients, P2P networks distribute the processing load across all nodes in the network. This means that each node has the same capabilities and authority as any other node, and there is no central point of control. Decentralization makes P2P networks more resilient and less susceptible to system failures or attacks, as there is no single point of failure.
Resource Sharing
Resource sharing is another key characteristic of P2P networks. In a P2P network, nodes can share resources such as files, bandwidth, and processing power with other nodes in the network. This means that users can access a wider range of resources than they would have access to on their own. In file-sharing applications, for example, users can download files from multiple sources, which can result in faster download speeds and increased availability of files.
Scalability
P2P networks are highly scalable, as they can grow or shrink dynamically as nodes join or leave the network. This means that P2P networks can accommodate a large number of nodes without affecting performance, and they can also continue to function even if some nodes go offline. P2P networks can also be easily extended to include new features or services without requiring a complete overhaul of the network architecture.
Anonymity
P2P networks can provide a high level of anonymity, as nodes do not need to identify themselves to other nodes in the network. This can be beneficial for users who wish to remain anonymous while accessing resources or communicating with other users. However, anonymity can also make it easier for malicious actors to engage in illegal activities such as copyright infringement, fraud, and cyber attacks.
Security
P2P networks can be both more and less secure than centralized networks, depending on the specific implementation. Because there is no central point of control, P2P networks can be more resilient to attacks such as denial of service (DoS) attacks, as there is no single target. However, P2P networks can also be vulnerable to attacks that exploit weaknesses in the protocol or in individual nodes. For example, a malicious node could insert malware into a shared file, which could then infect other nodes in the network.
Network topology
P2P networks can be organized in different topologies, such as pure P2P networks, hybrid P2P networks, and super-peer networks. In pure P2P networks, all nodes have equal capabilities and there is no hierarchy. In hybrid P2P networks, some nodes have higher capabilities or authority than others. In super-peer networks, some nodes act as hubs or servers that facilitate communication between other nodes in the network. The choice of topology depends on the specific requirements of the application and the size and complexity of the network.
Autonomy
P2P networks allow for greater autonomy, as users have more control over their own resources and can choose which resources to share and which to keep private. This can be beneficial for users who value their privacy or who want to maintain control over their own data. However, autonomy can also lead to a lack of coordination and cooperation among nodes, which can affect the overall performance of the network.
Types of P2P Network
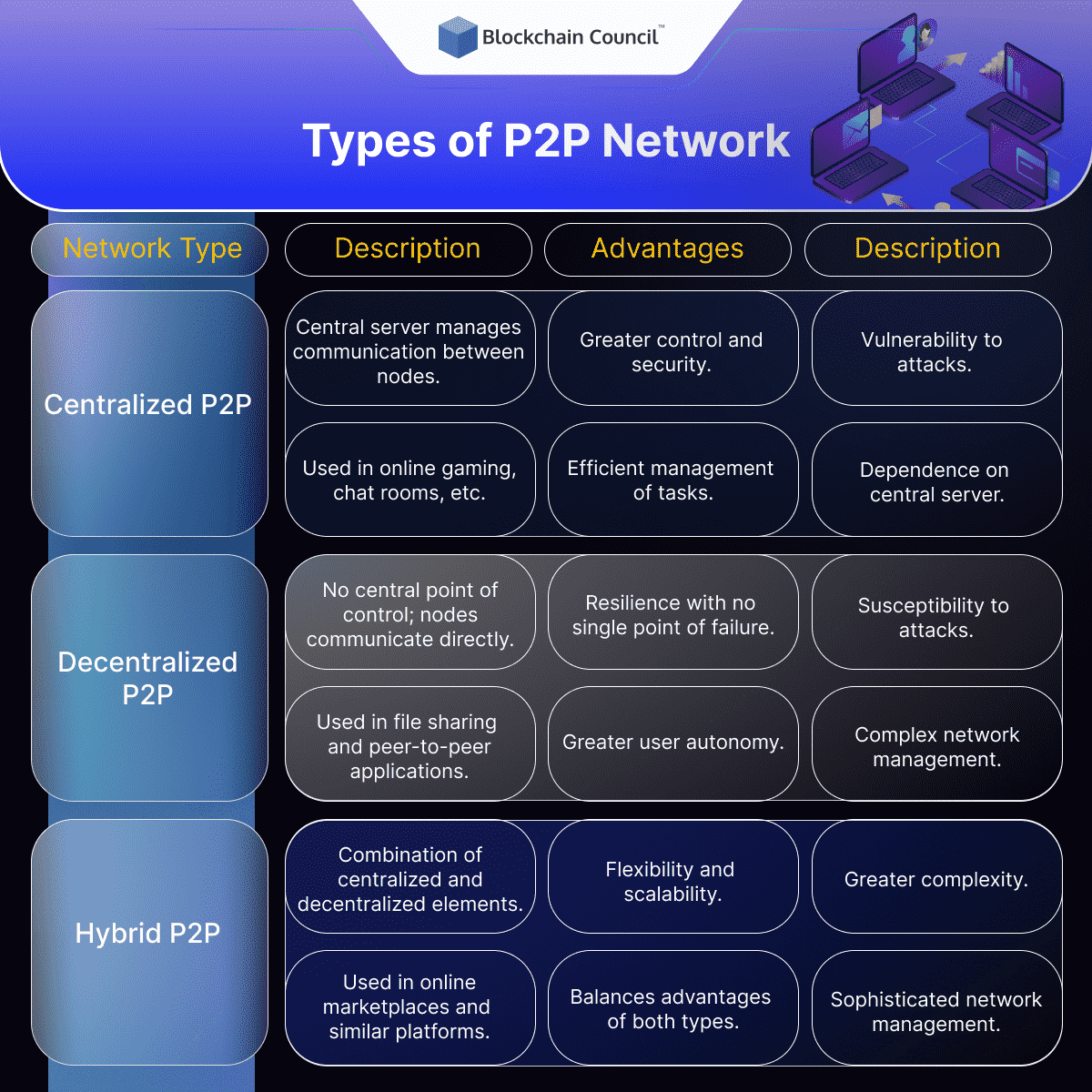
Centralized P2P Network
In a centralized P2P network, there is a central server or hub that manages all communication between nodes. Nodes in the network do not communicate directly with each other, but instead communicate through the central server. This type of P2P network is often used in applications such as online gaming and chat rooms, where a centralized server is needed to manage user authentication, content distribution, and other tasks.
Centralized P2P networks offer several advantages, including greater control and security, as the central server can monitor and regulate the network. However, they also have several drawbacks, including greater vulnerability to attacks and greater dependence on the central server.
Unstructured P2P Networks
Unstructured P2P networks, exemplified by protocols like Gnutella and Kazaa, are characterized by nodes that randomly form connections with each other. This ad-hoc structure allows for easy network building and robustness against high rates of churn (when peers frequently join and leave the network). However, this lack of a global structure can lead to inefficiencies. For instance, locating a specific piece of data requires flooding the network with queries, leading to high signaling traffic and processing loads, with no guarantee of finding rare data.
Structured P2P Networks
Structured P2P networks, on the other hand, organize their overlay into a specific topology. They commonly use Distributed Hash Tables (DHT) to efficiently locate files or resources, even rare ones. In these networks, each file is assigned to a peer using consistent hashing, allowing for efficient key-value pair searches within the DHT. Despite their efficient resource discovery, structured networks face challenges in highly dynamic environments where peers frequently join and leave, as they require maintaining updated neighbor lists.
Decentralized P2P Network
In a decentralized P2P network, there is no central point of control or authority. Nodes communicate directly with each other, and there is no hierarchy or structure to the network. This type of P2P network is often used in applications such as file sharing, where users share files directly with each other without the need for a central server.
Decentralized P2P networks offer several advantages, including greater resilience, as there is no single point of failure, and greater autonomy, as users have more control over their own resources. However, they also have several drawbacks, including greater susceptibility to attacks and greater difficulty in managing the network.
Hybrid P2P Network
In a hybrid P2P network, there is a combination of centralized and decentralized elements. Some nodes in the network act as hubs or servers that facilitate communication between other nodes, while other nodes communicate directly with each other. A notable example, until 2014, was Spotify. This type of P2P network is often used in applications such as online marketplaces, where a central server is needed to manage transactions and user authentication, but direct communication between users is also desirable.
Hybrid P2P networks offer several advantages, including greater flexibility and scalability, as the network can grow or shrink dynamically as nodes join or leave the network. They also offer a balance between the advantages and drawbacks of centralized and decentralized networks. However, they also have several drawbacks, including greater complexity and the need for more sophisticated network management.
Use Cases Across Different P2P Network Types
- Content Delivery and File Sharing: P2P networks are widely used for file sharing and content delivery. Technologies like Gnutella, G2, and eDonkey optimize performance and offer services such as cache improvement. They enable efficient distribution of multimedia content, games, and software.
- Multimedia Broadcasting: For audio and video delivery, some multimedia programs utilize P2P networks coupled with streaming servers. Educational projects like LionShare have been developed for the global exchange of multimedia files between institutions.
- Energy Trading: Innovative applications like energy trading are emerging, with companies like Power Ledger and Bovlabs using P2P technology to facilitate these transactions.
- Cryptocurrencies: P2P technology underpins the operation of cryptocurrencies such as Bitcoin, Ether, and Peercoin, demonstrating its utility in secure, decentralized financial transactions.
How P2P networks differ from traditional client-server networks
Peer-to-Peer (P2P) networks differ significantly from traditional client-server networks in several key aspects:
- Network Structure: In a P2P network, each node (computer or device) acts both as a client and a server, sharing resources directly with other nodes. In contrast, client-server networks have dedicated servers that provide resources or services to client computers.
- Decentralization: P2P networks are decentralized, meaning there’s no central point of control or distribution. This is different from client-server networks, where the server is the central point that clients depend on for resources and services.
- Resource Distribution: In P2P networks, resources like files or processing power are distributed across all participating nodes. In client-server networks, resources are centrally located and managed on the server.
- Scalability: P2P networks can scale more easily since adding new nodes increases the total resources of the network. Client-server networks may require significant server upgrades to handle increased client loads.
- Reliability and Fault Tolerance: P2P networks are generally more resilient to failures because there’s no single point of failure. In client-server models, if the server goes down, the entire network can be affected.
- Cost and Maintenance: P2P networks typically have lower costs and maintenance requirements as each node contributes to the network, whereas client-server networks require significant investment and maintenance for the server infrastructure.
Understanding these differences is crucial for anyone looking to delve into the world of networking, whether it’s through developing P2P applications or managing traditional client-server systems.
Advantages of P2P Network
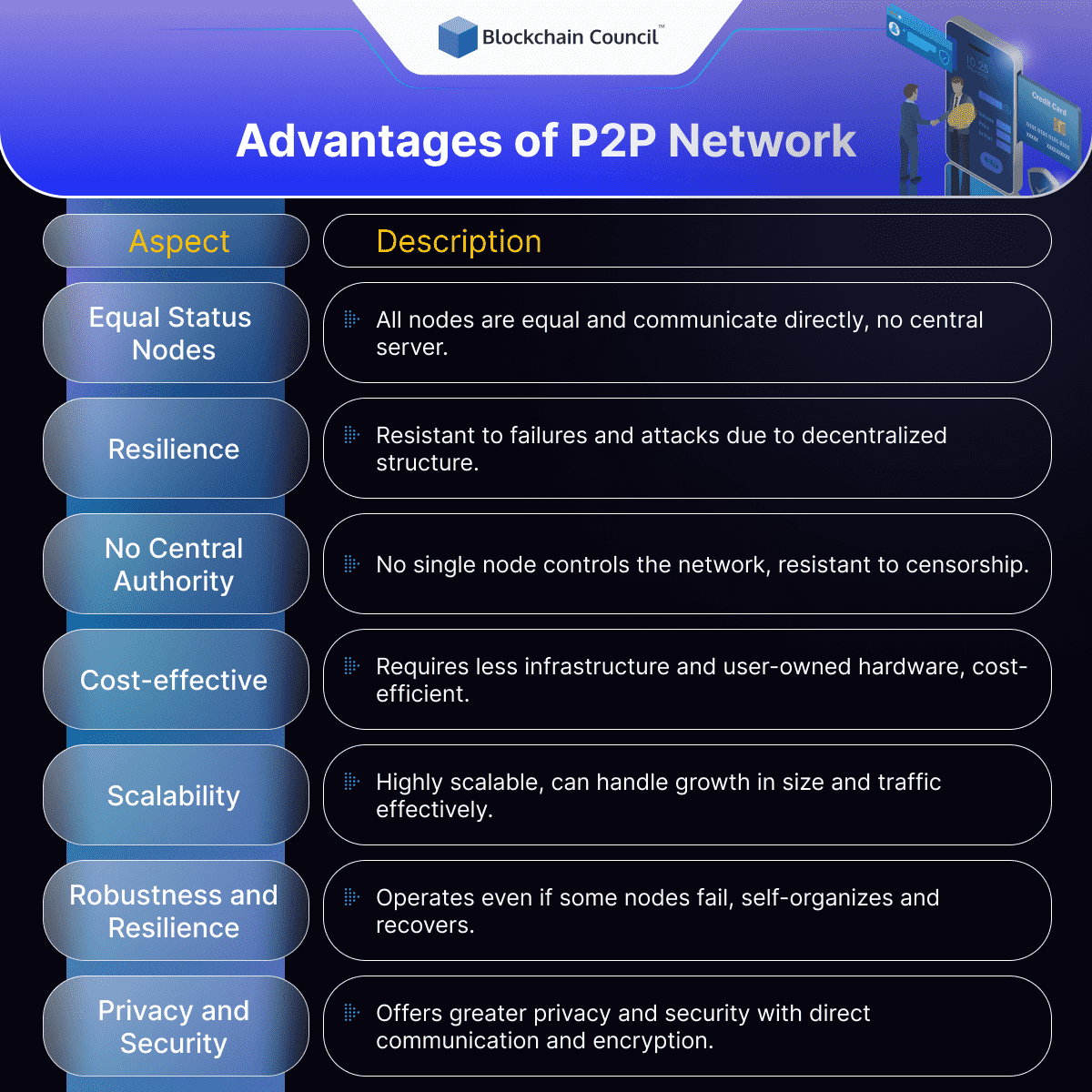
Distributed Architecture
In a P2P network, all participating nodes have equal status and can communicate with each other directly without the need for a central server. This distributed architecture makes P2P networks highly scalable, allowing them to handle large amounts of data and traffic without becoming overloaded.
Furthermore, P2P networks are resistant to failures and attacks since there is no central point of failure. In a traditional client-server network, a single server going down can render the entire network inoperable. In contrast, P2P networks can operate even if some nodes fail or leave the network, since other nodes can take over their responsibilities. This resilience is especially useful in distributed systems where it is difficult or expensive to guarantee the availability of a central server.
No Centralized Authority
In a P2P network, no single node has control over the network, making it more resistant to censorship, tampering, or failure. This decentralized structure also enables users to collaborate and share resources freely without being subject to the rules and restrictions of a central authority. This autonomy can be especially useful in applications where users want to exchange data or collaborate in a decentralized and open manner, such as in the case of open-source software development or decentralized marketplaces.
Cost-effective
P2P networks can be more cost-effective than client-server networks since they require less infrastructure and hardware. In a client-server network, the central server and associated hardware can be expensive to maintain, especially as the network grows. In contrast, P2P networks can rely on user-owned hardware to handle communication and storage, reducing the costs associated with maintaining a central server.
Furthermore, P2P networks can enable more efficient use of resources since nodes can share resources and collaborate more effectively without needing to access a central server. This can result in significant cost savings in applications that require large amounts of computing power or data storage, such as scientific computing or data processing.
Scalable
P2P networks are highly scalable since they can grow in size and handle more data and traffic without becoming overwhelmed. This scalability is due to the distributed architecture of P2P networks, which allows them to handle an increasing number of nodes without needing to rely on a central server.
Further, P2P networks can be more resilient to traffic spikes since they can distribute the load among the participating nodes, whereas in a client-server network, the central server can become a bottleneck during peak periods.
Robustness and Resilience
P2P networks are more robust and resilient than client-server networks since they can continue to operate even if some nodes fail or leave the network. This resilience is due to the distributed architecture of P2P networks, which ensures that there is no central point of failure. P2P networks can also self-organize and recover from failures since the participating nodes can take over the responsibilities of failed or absent nodes.
This robustness and resilience can be particularly useful in applications that require high availability and reliability, such as online marketplaces, e-commerce sites, or online gaming platforms.
Privacy and Security
P2P networks offer greater privacy and security than traditional client-server networks since they enable direct communication between nodes, making it more difficult for third parties to intercept or monitor communication. Furthermore, P2P networks often employ encryption and other security measures to protect users from malicious actors.
Moreover, P2P networks can be more resistant to attacks since they do not rely on a central server, making it more difficult for attackers to target a single point of failure. This decentralization makes P2P networks attractive for applications that require a high level of privacy and security, such as online voting systems, secure messaging apps, or decentralized marketplaces.
Disadvantages of P2P Network
While P2P networks offer several advantages over traditional client-server networks, such as faster downloads and lower costs, there are also several disadvantages that should be taken into account.
Difficulty in Implementation
Setting up a P2P network can be more complex and require more technical expertise than setting up a traditional client-server network. This is because P2P networks rely on a distributed architecture, which means that there is no central server to manage the network. Instead, each peer in the network is responsible for managing its own connections and sharing files with other peers. This can make it more difficult to set up and manage a P2P network, especially for users who are not technically savvy.
Network Management
P2P networks can be challenging to manage since they rely on the cooperation and contribution of the participating nodes. In a traditional client-server network, the network administrator can monitor and manage the network from a central location. With a P2P network, however, each peer is responsible for managing its own connections and file sharing, which can make it more difficult to troubleshoot network issues.
Managing the resources and data in a P2P network can also be challenging since nodes can join and leave the network at any time, making it difficult to ensure data availability and consistency. This lack of centralized control can also result in issues such as data duplication or inconsistency, which can affect the reliability and efficiency of the network.
Security Risks
P2P networks are known for their security risks, which can include the transmission of viruses and other malware. Since each peer can connect to any other peer on the network, there is a risk of malicious users infecting the network with viruses or other malware. Additionally, files shared on P2P networks may not be properly vetted for viruses or other security threats, which can put users at risk. Finally, since P2P networks are often used to share copyrighted content, users may also be at risk of legal action for copyright infringement.
Limited Control
In a P2P network, no single node has control over the network, making it challenging to enforce rules, policies, or standards. This lack of centralized control can result in issues such as data inconsistency, conflicting rules, or malicious behavior by some nodes.
Moreover, the distributed architecture of P2P networks can make it challenging to ensure compliance with regulations or legal requirements. For example, in applications such as online marketplaces or social networks, it can be difficult to enforce rules such as age restrictions, content moderation, or intellectual property rights.
Legal Issues
P2P networks are associated with a number of legal issues, particularly related to copyright infringement. Since they are often used to share copyrighted content, users may be at risk of legal action for copyright infringement. Additionally, many Internet Service Providers (ISPs) have policies in place that prohibit or restrict the use of P2P networks on their networks. This can make it more difficult for users to access P2P networks, or to use them without incurring additional costs or penalties.
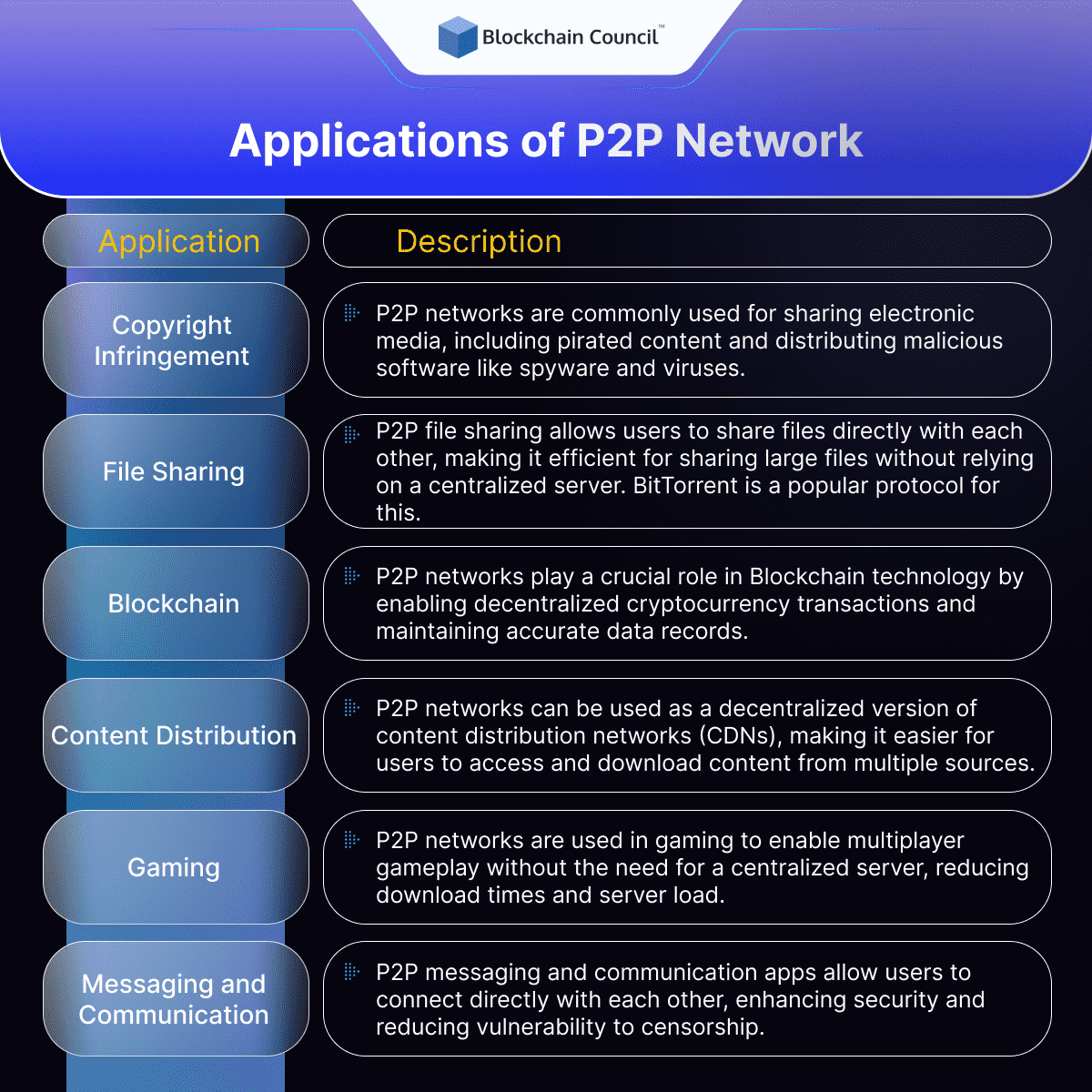
Applications of P2P Network
Peer-to-peer technology has undeniably paved the way for several other technologies that integrate with its architecture to provide greater and better services to users. Apart from Blockchain, which you can learn in any top-rated Blockchain class, there are various other applications of peer-to-peer networks.
However, there are few areas where P2P networks find quite different applications. Let us take you through some of the most common applications where peer-to-peer networks are predominantly used.
- Peer to peer and copyright infringement
The first and most obvious application of a P2P network is associated with copyright infringement. As these file-sharing networks use the devices from both the end of the client and the server, it becomes one of the most commonly used platforms for sharing electronic media, mostly for pirated content. In addition to this, these networks also find their application in distributing malicious software such as spyware and viruses.
It means that by installing any peer-to-peer file-sharing software on a device, anyone can access the files among millions of other users, irrespective of whether the person is doing it intentionally or not. However, with such networks, people who lawfully buy content online may also get in trouble. So, it is always advisable to take the necessary precautions.
Some prominent examples of such software include Frostwire, Kazaa lite, BitTorrent, Limewire, and Gnutella.
- File Sharing
P2P networks are widely used for file sharing. P2P file sharing allows people to share files with each other without the need of a centralized server. This means that users can send even large files quickly without worrying about bandwidth and server capacity. For instance, BitTorrent is a popular P2P file sharing protocol. It breaks large files into small pieces and distributes them quickly to multiple computers. Each computer in this network can download and share the files quickly. Internet Archive uses BitTorrent as its P2P file sharing protocol. The platform uses P2P file sharing to distribute books, music, movies available on public domains, making it easier for internet users to easily access such files.
- Blockchain
As a technology, a P2P network is based on the concept of decentralization. The foundational architecture of Blockchain technology similarly enables a user to transfer cryptocurrency across the globe without needing any middleman or intermediary. With such a decentralized distribution, it becomes easier for any individual to become a part of this process of verification.
When a peer-to-peer network is enabled on a Blockchain, the network helps in the maintenance of a complete replica of the records ensuring the accuracy of data. On the other hand, it also offers greater security as compared to conventional client-server systems. Therefore, a peer-to-peer network works phenomenally when used with Blockchain technology. If you wish to learn more about the foundational concepts of Blockchain, make sure to pick up the best Blockchain training platform for it.
- Content Distribution
Peer-to-peer networks are also used for content distribution. CDNs or content distribution networks are designed to distribute content to users from multiple servers. P2P networks can be used as a version of CDN. It will allow users to access and download content from anywhere without the need of one centralized server.
The Live Networks project is a type of P2P CDN. It uses a P2P network to distribute live video feeds of several events like sports and concerts. By distributing videos across multiple computers or nodes, the network is able to handle large volumes of traffic without overloading a single server.
- Gaming
P2P networks are also used in gaming. P2P gaming allows users to play games with one another without the need for a centralized server. In P2P gaming, each player’s computer acts as both a client and a server, allowing players to connect directly with one another and share game resources.
One popular P2P gaming platform is Steam, which allows players to download and play games from other players’ computers. This can help reduce download times and server load, making it easier to scale games to a large number of players.
Another example is Minecraft, a popular sandbox game that allows players to build and explore virtual worlds. Minecraft can be played in single-player mode, but also supports multiplayer mode through P2P connections. This allows players to collaborate on building projects or compete in games with one another.
- Messaging and Communication
P2P networks can also be used for messaging and communication. Messaging and communication applications that use P2P networks allow users to communicate directly with one another, without the need for a centralized server.
One example of a P2P messaging application is Tox, an open-source, encrypted messaging platform that allows users to send messages, make voice and video calls, and share files. Because the platform is decentralized, it is more secure and less vulnerable to censorship or surveillance.
Another example is Briar, a P2P messaging app that allows users to communicate without an internet connection. Briar uses Bluetooth or Wi-Fi to connect directly with other users in the same physical vicinity, making it ideal for situations where internet connectivity is limited or non-existent.
- Distributed Computing
Finally, P2P networks are used for distributed computing. Distributed computing is a type of computing where tasks are distributed across multiple computers. P2P networks can be used to create a distributed computing network, allowing users to contribute their computer’s processing power to a larger computing task.
One example of P2P distributed computing is the Folding@home project, which uses P2P networks to simulate protein folding and other complex molecular dynamics. Users can download the Folding@home software and contribute their computer’s processing power to the project, helping scientists to better understand diseases such as Alzheimer’s, Parkinson’s and cancer. The project has been successful in discovering new drug candidates and therapeutic strategies to combat diseases.
Another example of P2P distributed computing is the BOINC (Berkeley Open Infrastructure for Network Computing) project, which allows users to contribute their computer’s processing power to various scientific projects. These projects include research into climate change, astrophysics, and molecular biology. By contributing their computer’s processing power to these projects, users can help advance scientific knowledge and make important discoveries.
Case Studies and Real-World Examples
Analysis of Popular P2P Networks and Platforms
- qBittorrent, uTorrent, and BitTorrent: These platforms exemplify the power and functionality of P2P file-sharing software, facilitating the exchange of large files across the internet. Their widespread adoption demonstrates the efficiency of P2P networks in distributing data without the need for a centralized server.
- Seedr, eMule, and Frost Wire: These platforms are other notable examples of P2P software, showcasing the diversity and adaptability of P2P technology in various digital environments. They are designed to be user-friendly, ensuring that users on different platforms, including Windows, Mac, and Android, can easily participate in P2P networks.
Success Stories and Notable Failures
- Napster: A revolutionary music-sharing platform that became a household name in the early 2000s. Napster’s rise and subsequent legal battles over copyright infringement highlight both the potential and the pitfalls of P2P networks. While it was eventually shut down due to legal issues, Napster’s legacy continues to influence the way digital media is shared and distributed.
- Usenet: Often regarded as the earliest precursor to modern P2P networks, Usenet allowed users to post and exchange messages and news, similar to today’s online forums. Its decentralized nature set the stage for today’s P2P file-sharing systems.
Impact Assessment on Various Industries
- Music and Publishing Industries: P2P networks like Napster disrupted traditional distribution channels, challenging established business models and prompting industries to adapt. This led to the evolution of digital streaming services and self-publishing platforms like Amazon’s Kindle Direct Publishing and Smashwords, transforming how content is created, shared, and monetized.
- Transportation and Financial Services: The rise of ride-sharing services like Uber and Lyft and P2P lending platforms illustrates the disruptive impact of P2P networking on traditional business models. These platforms have democratized access to services and funding, creating new opportunities and challenges for regulatory oversight.
- Collaborative Consumption: P2P networking has propelled the sharing economy, with platforms like Airbnb, Zipcar, and WeWork revolutionizing how we think about ownership and resource utilization. This shift has significant implications for sustainability, community building, and the traditional concept of property and services.
- Empowerment of Individuals and Small Businesses: Platforms such as Upwork and Etsy have enabled individuals and small businesses to compete on a global scale, offering new avenues for entrepreneurship, freelancing, and crowdfunding. P2P networks have become instrumental in leveling the playing field, providing access to markets, resources, and networks previously limited to larger entities.
- Innovation and Creativity: The decentralized nature of P2P networks fosters innovation, as seen in the collaborative development platforms like GitHub and the rise of crowdfunding for creative projects. P2P networks have been crucial in empowering artists, developers, and entrepreneurs to bring their innovative ideas to life, challenging traditional creative and business practices.
What are peer to peer transactions?
Peer-to-peer (P2P) transactions are when two individuals or parties exchange money or assets directly with each other, without involving a middleman like a bank or payment service. Here’s how it works:
- Agreement: Both parties agree on the terms of the transaction. This includes what’s being exchanged (money, goods, services), the quantity, and any conditions.
- Transfer: They transfer the money or assets directly. This can be done in various ways, such as cash, check, bank transfer, or through digital payment apps like Venmo, PayPal, or cryptocurrencies like Bitcoin.
- Confirmation: Once the transfer is complete, both parties confirm that the transaction has taken place. In the case of digital transactions, there’s often a record or receipt for proof.
- Security: While P2P transactions can be convenient, it’s crucial to be cautious and only transact with trusted individuals. Scams can happen, so always double-check details before proceeding.
- Privacy: P2P transactions can offer more privacy compared to traditional methods because they don’t always involve disclosing personal information to a third party.
P2P transactions are commonly used for various purposes, including splitting bills with friends, buying and selling items online, or sending money to family members. They provide a direct and straightforward way for people to exchange value without the need for intermediaries.
Future of P2P Network
Recent Technological Advancements in AI and P2P Networks
Peer-to-peer (P2P) networks have evolved significantly, adapting to the demands of highly distributed IT environments. Organizations now integrate applications across various platforms, from private data centers to public clouds and edge locations. This shift has expanded attack surfaces and heightened the risk of cyberattacks, necessitating innovative network technologies and frameworks for secure, efficient connectivity.
A pivotal advancement in P2P networks is the integration of network automation and Artificial Intelligence Operations (AIOps). With the surge in devices and remote work, managing the network has become increasingly complex. Many organizations have adopted network automation for repetitive tasks, but the complexity of distributed environments demands more. Here, AI and Machine Learning (ML) technologies, especially adaptive AI, play a crucial role. They process and analyze network information to provide real-time actionable insights, including troubleshooting and predictive analysis. This shift towards AI/ML in network management marks a significant stride in the evolution of P2P networks.
Integration with Emerging Technologies
The convergence of network and security has emerged as a key trend. With the adoption of Zero Trust and Secure Access Service Edge (SASE) frameworks, the network is now a vital tool in identifying and preventing cyberattacks. This convergence facilitates secure connectivity across various sites and is integral to modern P2P networks.
Moreover, the rise of multi-cloud networking reflects the growing dependence on multiple public clouds. This technology simplifies connecting to various cloud vendors, mitigating the complexity and skill gaps associated with cloud and IT architecture. Multi-cloud networking is becoming a must-have technology in P2P environments, streamlining the deployment and movement of applications across different clouds.
Other Advancements in Technology
Blockchain-based P2P networks are a prime example of how advancements in technology are enabling new use cases for P2P networks. For instance, Blockchain technology can provide a secure and transparent way to track and verify transactions without the need for a central authority. This is exemplified by cryptocurrency, which is enabled by Blockchain technology and allows for secure and decentralized transactions.
With the rise of cloud computing, P2P networks can be used to share resources in a decentralized and transparent manner, leading to more efficient use of resources and cost savings. A good example of this is Golem, which is a decentralized P2P network that allows users to rent out computing power for various purposes, such as rendering graphics or scientific computing.
Emerging Trends and Use Cases
One of the most exciting emerging trends in P2P networks is the use of decentralized social networks. These networks, which are built on P2P infrastructure, provide greater privacy and control for users, as well as the ability to own and control their data. An example of this is Mastodon, a decentralized social network that allows users to create their own instances and communicate with other users across the network.
For example, P2P networks can enable more efficient and secure cloud computing by allowing users to share resources and data in a decentralized and transparent manner. Similarly, P2P networks can offer more privacy and control in social networking, as well as new opportunities for online marketplaces and e-commerce.
Another emerging use case for P2P networks is in online marketplaces and e-commerce. P2P networks can enable direct transactions between buyers and sellers, without the need for intermediaries such as online marketplaces or payment processors. An example of this is OpenBazaar, which is a decentralized marketplace that allows users to buy and sell goods and services directly with each other.
Future Outlook
Looking forward, the delineation of private 5G and Wi-Fi use cases will significantly influence P2P network technologies. Organizations are evaluating these technologies for specific applications, with industrial use cases favoring 5G and enterprise environments continuing to rely on Wi-Fi 6/6E. This choice between 5G and Wi-Fi will shape future network deployments and strategies.
Additionally, the adoption of digital twin technology is set to increase in networking. This technology enables the creation of a virtual network environment, mirroring the physical network. It allows network operations teams to test changes virtually, enhancing business resiliency and preemptively addressing potential issues. The use of digital twins signifies a move towards more proactive and efficient network management.
These technological advancements and integrations with emerging technologies like AI, IoT, and 5G are shaping the future of P2P networks. As these networks continue to evolve, they will offer more robust, secure, and efficient solutions for the increasingly complex and distributed digital world.
Challenges and Opportunities
One of the key challenges facing P2P networks is scalability. P2P networks can be difficult to scale efficiently, particularly as the number of users and transactions increases. This challenge is being addressed through new protocols and frameworks, such as IPFS and DAT, which can enable more efficient and scalable P2P networks.
Another challenge facing P2P networks is security risks, particularly as the networks are often open and decentralized. However, new developments in encryption and security protocols are helping to mitigate these risks, and P2P networks can provide greater security and privacy than traditional centralized networks.
AI in Peer to Peer Network Operations
AI-driven Node Discovery and Network Formation
In the dynamic landscape of Peer-to-Peer (P2P) networking, AI plays a critical role in enhancing node discovery and network formation. Enterprises are increasingly deploying AI as a tool for safeguarding against potential security threats and for network management, particularly in complex, distributed networks. AI’s capability to process extensive amounts of data surpasses human capacity, making it essential for managing intricate systems like 5G networks. AI systems can efficiently monitor network performance, anticipate potential issues, and even troubleshoot problems autonomously, without human intervention.
AI in Data Storage, Retrieval, and Routing Mechanisms
The integration of AI into P2P networks significantly boosts the efficiency of data storage, retrieval, and routing processes. AI for IT operations (AIOps), which involves using AI technologies such as machine learning to automate tasks, is seeing a rapid increase in adoption. This trend is driven by the complexities of digital transformation, where the volume of data generated and the need for its analysis, monitoring, and management becomes overwhelming for human capabilities. The application of AI in these areas helps in replacing traditional monitoring tools, adapting to the post-pandemic environment where practical outcomes are paramount.
Impact of AI on Network Efficiency and Data Management
AI’s impact on network efficiency and data management is profound. It provides enhanced visibility for network management, identifying anomalies and streamlining the focus of network teams on critical performance and security issues. This aspect of AI is crucial in data centers and is expanding to other network environments. Additionally, AI capabilities are being integrated into software-defined WANs (SD-WAN) and Secure Access Service Edge (SASE) providers to improve traffic direction, optimize delivery, and assist in troubleshooting.
5G carrier networks, characterized by their constantly changing variables, benefit significantly from AI. AI aids in managing the massive influx of data and supports the provisioning process in these dynamic environments. The role of AI in these networks will become more pivotal as we advance in deploying 5G technology and require more granular control over connections and switching.
However, it’s essential to recognize that AI and machine learning are not intended to replace human intervention entirely. While they can alert, recommend, and automate certain processes, physical issues in networks still require human attention. The progression in leveraging AI technology in P2P networks is moving towards full automation, with a significant proportion of enterprises currently in the alert-and-recommend stage, using AI to enhance their operational efficiency.
How an AI Certification Can Help You in the Field of P2P Networks
Peer-to-peer (P2P) networks are evolving rapidly, thanks to the integration of Artificial Intelligence (AI). We have already explored how artificial intelligence is shaping the future of peer-to-peer networks. These AI-enhanced P2P systems are at the forefront of a technological revolution, offering a decentralized, resilient, and efficient network architecture. Unlike traditional networks reliant on central servers, P2P AI systems leverage AI to process and analyze data directly on network devices. This innovation results in reduced latency, improved privacy, and the ability to function independently of continuous internet connectivity.
The transformative power of AI in P2P networks is redefining device communication and computation. Traditional network setups, where data processing occurs through central servers, often lead to bottlenecks and inefficiencies. P2P AI systems circumvent these issues by enabling devices to share and analyze data directly among themselves. Utilizing distributed computing and AI algorithms, these systems facilitate local decision-making, which speeds up response times and reduces network congestion.
Moreover, in an era where data privacy and security are paramount, P2P AI systems offer a viable alternative to conventional models. Data processing within these networks occurs locally, significantly reducing the need to transmit sensitive information over the internet and thus enhancing privacy. The decentralized nature of P2P AI systems also eliminates single points of failure, augmenting network resilience and security.
As we look to the future, the role of P2P AI systems in shaping the technological landscape is increasingly prominent. They hold great promise in redefining norms of communication, computation, and privacy, steering us towards a more efficient, secure, and user-centric digital world. However, challenges such as regulatory compliance and interoperability need addressing to fully unlock their potential.
In light of these advancements, understanding AI becomes crucial for those interested in the future of networking. This is where our AI guide and certification programs by the Blockchain Council come into play. These resources are designed to provide a comprehensive understanding of AI and its application in various domains, including P2P networks. By exploring our AI certifications, readers can gain the knowledge and skills necessary to innovate and excel in this rapidly evolving field. We encourage all our readers to delve into these resources to enhance their understanding and contribute to the future of P2P networks and AI.
Conclusion
With reference to our above discussion, it is clear that peer-to-peer network is one of the most sophisticated technologies that we have today. What makes it even more prominent is its link with Blockchain, AI and the potential it holds in terms of its usability. However, it is equally important to know and understand that it may not always come to use for the right reasons due to such open and easy access to all types of content. While it can be a possible argument that this technology should not be promoted, we as individuals must understand our responsibilities as users while accessing online content.
FAQ
What is a peer to peer network?
- A peer to peer (P2P) network is a decentralized network architecture where individual nodes in the network can function both as a client and as a server.
- It allows them to share and access resources directly with other nodes in the network without the need for a centralized authority or intermediary.
What are the advantages of P2P networks?
- P2P networks have several advantages, including their distributed architecture, lack of a centralized authority, cost-effectiveness, scalability, and robustness and resilience.
- They also offer greater privacy and security compared to traditional centralized networks.
What are the different types of P2P networks?
- There are three main types of P2P networks: centralized, decentralized, and hybrid. In centralized P2P networks, there is a central server that maintains control over the network.
- In decentralized P2P networks, there is no central authority, and nodes in the network are equal. Hybrid P2P networks combine aspects of both centralized and decentralized networks.
What are some real-life examples of P2P networks?
- Some real-life examples of P2P networks include cryptocurrency networks like Bitcoin, file-sharing networks like BitTorrent.
- It also includes computing resource-sharing networks like Golem.
What are some of the challenges facing P2P networks?
- P2P networks can be difficult to scale efficiently as the number of users and transactions increases, and there are also security risks associated with the decentralized nature of these networks.
- However, advancements in technology and encryption protocols are helping to mitigate these challenges.





































































 Guides
Guides News
News Blockchain
Blockchain Cryptocurrency
& Digital Assets
Cryptocurrency
& Digital Assets Web3
Web3 Metaverse & NFTs
Metaverse & NFTs
