
- Ayushi Abrol
- July 27, 2022
Private keys and public keys are among the most commonly used terms in the domain of cryptography and blockchain development. A method of facilitating communication between the sender and the receiver, cryptography involves two main mechanisms namely, encryption and decryption using a unique key. This is where the roles of private and public keys come into the scenario.
But have you ever wondered, what exactly is the difference between and what purpose do they serve?
Let us explore these questions in detail.
What is a Private Key?
Most commonly known as a secret key, a private key is an important element used in cryptography along with the relevant algorithm to encrypt and decrypt data. These keys are meant to be shared only between the user who generates them and the user with the authorization to decrypt the data. A private key is like a unique password, consisting of a series of letters and numbers.
Typically, a private key is generated randomly following a user-generated sequence of bits that cannot be easily traced or guessed. Since these are significantly longer, the length and complexity of private keys play a central role in determining how an outsider or potential attacker can access the data while trying to make a pair of keys that can work out until the right pair is identified and put into use.
These have an important role to play in mechanisms such as symmetric cryptography and asymmetric cryptography. We will explore these concepts later in the upcoming sections. For detailed insights on this, you can join a reliable blockchain course to get the best guidance.
How Does it Work?
A private key plays a significant role in data encryption. It is like an extremely large number applied for cryptography that resembles the structure of a password.
However, the scope of functions that a private key serves goes much beyond that. The functions of a private key also depend on its applications. These are unique to applications such as online verification and digital signature authorisation. For instance, it works in the following ways for asymmetric cryptography:
- For this, a private key uses encryption applications to generate key pairs through a source of randomness.
- Once the pair is generated, it is important to store the private keys securely on the cloud or offline. However, this must be protected with a password for better security.
- The next role is a key exchange where it looks out for a pair with public keys for applications such as cryptography and digital signatures.
- Once the above-mentioned process is completed, the user of a public key pair uses a private key to decrypt data. However, it is important to note that only the owner of a private key will be able to decrypt data using the public key. For purposes such as digital signatures, the user of a key pair can use their private keys to encrypt signatures. This is how anyone who holds access to that public key will be able to decrypt the signature and verify the same for authentication. One can also learn more on these from the best blockchain certification courses available online.
Why are Private Keys Used for Encryption?
Private keys offer several useful features over public keys. Due to this reason, it finds its application for encryption purposes. Here are a few reasons why:
- Better security
Private keys offer better services and features in terms of security. It is due to this reason that it is an ideal option for encryption.
- Faster and convenient
Another reason why private keys are ideal for encryption is that it makes the entire processing faster. Symmetric key encryption becomes computationally quicker than the other encryption mode with the help of a private key.
- Data transmission
Private keys are ideal for encryption also because it complements the required algorithm. It is also the reason that several cryptographic processes use private key encryption to facilitate data transmission. Therefore, the resulting ecosystem helps a user transfer data at a faster pace and with better security features.
What is a Public Key?
Similar to the concept of a private key, a public key is also a large numeric value commonly used to encrypt the data. A user can generate a public key through any software program. However, it is most commonly provided by a reliable authority responsible to make it available to the public through an easily accessible channel. If you wish to get yourself groomed on your blockchain basics, we would recommend blockchain learning opportunities for better clarity.
However, an important conceptual note here is that it is also used to encrypt a message or verify the authenticity of a digital signature. The mechanism applied here is quite different from that used in a private key where a single key is used between the sender and the receiver. Private keys are commonly used to decrypt messages that are generated using a public key to create digital signatures. However, a public key does not work as a single component. Rather, it functions as two distinct keys where one is used to encrypt the data and the other one is used for decryption.
How Does it Work?
A public key uses an algorithm mechanism called asymmetric mechanism to perform its primary function. Through this mechanism, two different keys are used for encryption and decryption. One of these public keys is used to encrypt messages while the other private key decodes them.
Where are Private and Public Keys Used?
Since public and private keys have their functionalities and features, they are used for a variety of purposes. Here are the most common applications of public and private keys:
-
Verification of digital signatures
One of the most common uses of public and private keys is verifying digital signatures. It is also an integral component of blockchain technology training requirements. It is mostly used by organizations to perform functions such as authenticate proof of a message, validity of software, digital document or check for authentication. The most important aspect to consider is that creating a digital signature needs public key encryption.
To facilitate the same, the sender is required to digitally sign the message using their private key. Once the process gets completed, the receiver then uses a public key to decrypt the message. Thus, public and private keys have an important role to play in facilitating and verifying digital signatures on both ends.
-
Facilitating safe and secure communication
Public and private keys are also necessary to ensure safe and secure communication while maintaining the confidentiality of sensitive data. Securing communications is another critical aspect of public and private key encryption. In such a scenario, people usually use public-key cryptography to ensure that the confidentiality of their digital content remains the same. The sender has to lock the data with their public key and only the intended receiver with the right private key will have access to it.
-
Enabling password authentication key agreement
Apart from playing the central role in verifying digital signatures and facilitating secure communication, private and public keys also help significantly towards enabling password authentication key agreement. A password-authenticated key agreement is a method where two or multiple parties can make cryptographic keys based on words belonging to one or more parties.
For instance, if a person wants to communicate a secret message to the other person, and or she gets the password belonging to that person, encrypts the message and uses it for a private key. In this way, when the first person sends a message encrypted with that key, the intended recipient will be able to decrypt and open it as they already have the password.
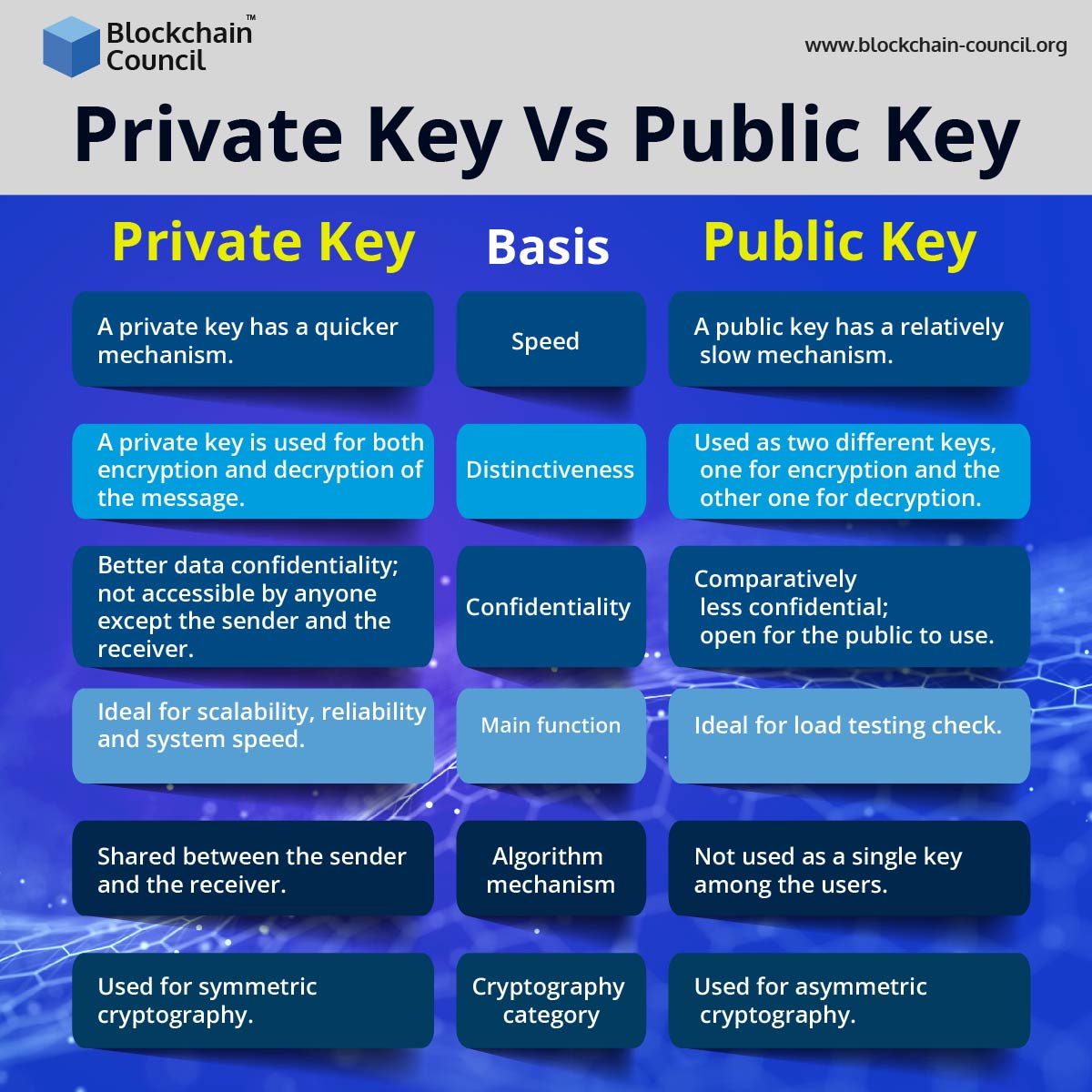
What are the Main Differences Between the Two?
Although both private and public keys play an important role in data encryption, they differ a lot in terms of their features and functionalities. You may come across this concept in many certified blockchain technology courses. However, it is also necessary to get the basic idea. Thus, the role they play is significantly important, it also becomes necessary to understand the thin line of difference between them.
Here are a few grounds to consider the main differences between the two:
- Speed factor
The first and most basic difference between public and private keys is their speed. A private key is considerably faster than a public key.
- Distinctiveness
Another distinguishing factor between a private key and a public key is their uniqueness. A private key is used for both encryption and decryption of the message as it is commonly used for symmetric key cryptography. However, it is not the same case with a public key. It is because a public key, which is used for asymmetric key cryptography uses 2 different keys. One of these is used for encryption while the other one is used to decrypt on the recipient’s end.
- Confidentiality
While referring to the functions of a public key and private key, it is also necessary to address the issue of confidentiality and security. With the private key, it is easier to maintain the confidentiality of messages or data as it is shared only between the sender and the receiver. However, the same confidentiality cannot be maintained with a public key as it is open and free to use for everyone to view the data.
- Main functions
One of the most notable differences between public keys and private keys is the main function they serve. A private key performance testing usually checks its scalability, reliability and system speed. However, a load testing check is ideal in the case of a public key. On the other hand, a user would need a private key to decrypt data received from the sender’s end. A user will be able to view the message using it but they will still need a private key to decrypt it.
- Algorithm mechanism
Another difference between the two types of keys is the mechanism they use. As mentioned earlier, a private key is used for both encryption and decryption of data. Therefore, it is openly shared between the sender and the receiver. However, a public key is used only for data encryption. Thus, cannot be used to decrypt the data as a private key would be required for that.
- Cryptography category
The two types of keys also differ based on the cryptographic category they can be used for. For instance, a private key is most commonly used for symmetric cryptography where a single key is required to transmit data between two users. On the other hand, in the case of a public key, it is open for everyone to view and uses an asymmetric mechanism. This mechanism is entirely different from that of a private key.
If you wish to learn blockchain technology with greater depth, we would recommend you join an authorized platform.
An Overview of the Differences
Let us take a brief overview of the differences we discussed above:
Final Takeaway
As a field in itself, cryptography has witnessed exponential growth over the years becoming an even more secure ecosystem as the blockchain platform itself. Having understood the important role that private and public keys play in cryptography, we can now have a clear idea of how the two terms differ. We hope this guide helped you get your concepts clear!


































































 Guides
Guides News
News Blockchain
Blockchain Cryptocurrency
& Digital Assets
Cryptocurrency
& Digital Assets Web3
Web3 Metaverse & NFTs
Metaverse & NFTs
