
- Toshendra Kumar Sharma
- January 18, 2025
There is no doubt that Blockchain is causing significant disruptions across almost all industry verticals that are in existence. Blockchain technology makes it possible to create a wide array of new business models. Blockchain is credited with being the sole technology since the invention of the internet brought about valuable innovations such as decentralization and trustless networks. Using tokens is one of the significant factors, out of the many, which have contributed to the success of Blockchain technology. This article will delve deeper into the concept of tokens and help you gain a clear picture of security tokens, and utility tokens. Also, you will be learning about the difference between these tokens. So, let’s begin!
Overview
The term “Blockchain” can be confusing itself, and so are its terminologies. Talking about tokens, coins, and cryptocurrency, they all are considered one thing by most people. However, they all have their own functionality, which differs from each other. Tokens are of a few types. Here we will be discussing security tokens, utility tokens, and NFT. Security tokens are a form of investment, and anyone can utilize utility tokens for a particular service or product. On the other hand, a Non-fungible Token is a unique type of token and a collectible token. It is a form of art where artists can monetize their work. The prices of NFT are significant and can have extraordinary value.
Here, we are going to discuss all these tokens in detail and what is the use of tokens in the Blockchain industry.
Understanding Tokens
A token may simply refer to any given cryptocurrency token or a token that exists on another cryptocurrency’s Blockchain in computer security and cryptocurrency. A token is an asset, utility, or unit of value that a company issues. Tokens represent programmable assets or access rights which are managed through a smart contract and an underlying distributed ledger.
These are issued when a company launches an Initial Coin Offering (ICO), which is more or less the same as the Initial Public Offering (IPO). The main difference between an IPO and an ICO is that in an IPO, you receive stock in exchange for the investment you will make, whereas in an ICO, you will receive a token in exchange for your investment. Tokens can be redeemed to access the product or service of a company in the future.
What Are Security Tokens?
Security tokens are digital assets that derive their value from an external asset that can be traded. These are subject to Federal laws that govern security. It is mandatory for the security tokens to comply with these regulations. Failure to comply would lead to severe consequences such as penalties and potential derailment of the development of the project.
These depict assets such as participation in real physical underlyings earnings streams, companies, or entitlement to interest payments or dividends. In terms of economic function, these are the same as bonds, derivatives, and equities. If the startup abides by the regulatory requirements, security tokens offer a wide array of applications. These are also known as securitized tokens. Security Token Offering (STO) is built to increase the trust of the investor to invest in various projects.
- Security tokens authenticate identities electronically by storing personal information.
- They are issued by Security Token Services (STS), which authenticate the person’s identity.
- They may be used in place of or in addition to a password to prove the owner’s identity.
- Security tokens are not always secure—they may be lost, stolen, or hacked.
How does Security Token Work?
Security tokens are created as investments. Dividends in the form of additional coins are given to token holders each time the issuing company of the tokens earns a profit in the market. Users who hold the security token will also gain ownership of the company. Blockchain provides a platform that can be used to create a voting system that allows investors to exercise control over the decision-making process of the company. In short, a cryptocurrency token that passes the Howey Test is deemed a security token. They derive value from an external tradeable asset. As these tokens are deemed a security, they are subjected to federal securities and regulations. The Howey Test was determined by the Supreme Court to determine whether certain transactions qualify as “investment contracts.” If so, those transactions are considered securities under the Securities Act of 1933 and the Securities Exchange Act of 1934 and are subject to certain disclosure and registration requirements. In the USA, Security Tokens are subjected to regulations such as:
Regulation D
This will allow a particular offering to avoid being registered by the SEC-provided “Form D” that has been filled by the creators after the sale of the securities. The individual who offers this security may solicit offerings from investors in compliance with Section 506C. This section needs
verification stating that the investors are accredited and that the information provided during the solicitation is free from misleading or false statements.
Regulation A+
This allows the creator to offer SEC-approved security to non-accredited investors through a general solicitation of up to $50 million in investment. When compared to other options, this regulation may take more time compared to other options for the requirement to register the security. Due to this reason, this regulation will be more expensive than any other option.
Regulation S
This regulation is for any security offering which is executed in any country apart from the US and is not subjected to the registration requirement under section 5 of the 1993 Act. The creators will still need to follow the security regulations of the country where they will be executed.
On the other hand, utility tokens are not intended to give their holders the ability to control the decision-making process of a company. They aid users in interacting with a company’s services. Utility tokens are also not subjected to any regulations.
Having differentiated security tokens and utility tokens based on regulations, intended use, and functionality, let us now learn the three other crucial areas of distinction.
Role of Security Tokens
The role of security tokens revolves around providing a digital representation of ownership or investment in real-world assets while adhering to securities regulations. Here’s a straightforward breakdown:
- Asset Tokenization: Security tokens tokenize real-world assets, such as real estate, company shares, or other traditional financial instruments. This involves converting the rights to these assets into digital tokens on a Blockchain.
- Legal Compliance: One of the primary roles of security tokens is to comply with securities regulations. By adhering to these laws, security tokens ensure that the issuance, sale, and transfer of ownership are done in a legally compliant manner, protecting both issuers and investors.
- Ownership Representation: Security tokens represent ownership or a stake in an underlying asset. Holders of these tokens have legal rights tied to the asset, such as dividends, voting rights, or a share in profits.
- Efficient Transfer of Ownership: Blockchain technology enables efficient and transparent transfer of ownership. Security tokens streamline the process of buying and selling assets, reducing paperwork and administrative hurdles associated with traditional securities transactions.
- Increased Liquidity: By enabling secondary trading on compliant security token exchanges, security tokens contribute to increased liquidity for traditionally illiquid assets. Investors can buy and sell these tokens more easily than the physical assets they represent.
- Global Accessibility: Security tokens can be traded globally, providing access to a broader investor base. This global accessibility is facilitated by the decentralized nature of Blockchain technology, allowing for cross-border transactions.
- Automated Compliance: Smart contracts embedded in security tokens automate compliance with contractual and legal obligations. This can include the automatic distribution of dividends, execution of voting rights, and other functions, reducing the need for intermediaries.
- Fractional Ownership: Security tokens enable fractional ownership of high-value assets. Investors can own a fraction of an asset, making it more accessible to a wider range of investors who might not have the means to purchase the entire asset.
- Innovation in Fundraising: Security tokens offer new possibilities for fundraising, such as Security Token Offerings (STOs). These regulated fundraising methods provide companies with a way to raise capital by offering security tokens to investors.
Security Tokens Issues and Challenges
Security tokens, despite offering advantages in terms of digitizing ownership and complying with securities regulations, also face certain issues and challenges. Here’s an overview of some common challenges associated with security tokens:
- Regulatory Compliance: Ensuring compliance with securities regulations is a significant challenge for security tokens. Regulatory frameworks can vary globally, and navigating these complexities requires substantial legal expertise and resources.
- Legal and Regulatory Clarity: The regulatory landscape for security tokens is still evolving, and there may be uncertainties regarding how existing laws apply to these digital assets. A lack of clear and consistent regulations can create challenges for issuers and investors.
- High Initial Costs: The process of tokenizing securities and conducting regulated offerings, such as Security Token Offerings (STOs), involves significant legal and compliance costs. These high initial costs can be a barrier for smaller companies or startups looking to tokenize assets.
- Liquidity Concerns: While security tokens aim to enhance liquidity for traditionally illiquid assets, achieving this goal can be challenging. The success of secondary markets for security tokens depends on factors like market infrastructure, investor interest, and regulatory support.
- Educational Barriers: Investors and market participants may lack understanding of security tokens and how they differ from traditional securities. Educational efforts are needed to increase awareness and facilitate broader adoption of security tokens.
- Custody and Security: Safeguarding digital assets is crucial. Security tokens rely on secure Blockchain technology, but concerns about cybersecurity, hacks, and secure custody solutions remain important considerations for both issuers and investors.
- Market Fragmentation: The security token market may face fragmentation due to different Blockchain platforms and standards. The lack of interoperability among different security token protocols can hinder the seamless transfer of tokens across platforms.
- Token Standardization: The absence of standardized tokenization frameworks and protocols can complicate the integration of security tokens across different platforms and exchanges. Standardization efforts are essential for promoting consistency and compatibility.
- Slow Adoption: The traditional financial industry has been slow to adopt security tokens due to concerns, skepticism, and regulatory uncertainties. Overcoming resistance and encouraging institutional participation are ongoing challenges.
- Market Perception: Security tokens may face challenges in terms of perception, as some investors may associate them with a higher degree of risk or complexity compared to traditional securities. Building trust and credibility is crucial for wider acceptance.
What Are Utility Tokens?
Utility tokens are user tokens or app coins. This is a token that is given out during crowd sales as a project executes an ICO. When a company creates a utility token, it means that it is essentially creating a form of a digital coupon that can be redeemed in the future for discounted fees or special access to a product or service. Unlike security tokens, utility tokens are not used as investments as they can be exempted from the federal laws governing securities if they are properly set up. Examples of utility tokens are Filecoin, Siacoin, Civic, etc.
How Does a Utility Token Work?
A utility token is a type of cryptocurrency that has a specific purpose within a Blockchain ecosystem. It’s called a “utility” token because its primary function is to provide access to a particular product or service on a Blockchain platform.
Here’s a breakdown of how it works:
- Token Creation: The utility token is created through a process called an Initial Coin Offering (ICO) or Token Generation Event (TGE). During this event, people can buy these tokens using other cryptocurrencies like Bitcoin or Ethereum.
- Smart Contracts: Utility tokens often operate on Blockchain platforms that support smart contracts (self-executing contracts with the terms of the agreement directly written into code). These smart contracts define the rules and conditions of the utility token.
- Access to Services: The main purpose of a utility token is to provide access to a specific service or product within the Blockchain platform. For example, it could grant access to use a particular software, participate in a decentralized application (DApp), or get special privileges within a network.
- Limited Functionality: Unlike other types of cryptocurrencies, utility tokens usually don’t represent ownership in a company or share in profits. Their value is tied to their functionality within the ecosystem.
- Token Exchange: Utility tokens can be traded on cryptocurrency exchanges. The value of a utility token may fluctuate based on supply and demand dynamics, as well as the success and popularity of the associated platform.
- Use and Redemption: Users can use utility tokens to pay for services or products within the platform. In some cases, tokens may also be redeemable for specific benefits or discounts.
- Community Participation: Holders of utility tokens often have a say in the development and decision-making processes of the platform. This is because some Blockchain projects incorporate governance mechanisms that give token holders voting rights.
Roles of Utility Tokens
Utility tokens serve a specific purpose within a Blockchain ecosystem, providing access to a particular product or service. Here’s a straightforward breakdown of their role:
- Access to Services: The primary role of utility tokens is to grant access to specific services or products within a Blockchain platform. These tokens act as a form of digital currency that users can use to pay for and access functionalities offered by the platform.
- Token Creation: Utility tokens are created through Initial Coin Offerings (ICOs) or Token Generation Events (TGEs). During these events, users can purchase utility tokens using other cryptocurrencies, like Bitcoin or Ethereum.
- Smart Contracts: Many utility tokens operate on Blockchain platforms that support smart contracts. These contracts define the rules and conditions of the utility token, ensuring that they are used for their intended purpose.
- Limited Functionality: Unlike security tokens, utility tokens typically do not represent ownership in a company or share in profits. Instead, their value is tied to their functionality within the platform, and they are often designed to be used solely for accessing specific services.
- Token Exchange: Utility tokens can be traded on cryptocurrency exchanges. The value of these tokens may fluctuate based on supply and demand dynamics, as well as the success and popularity of the associated platform.
- Redeemable for Services: Users can use utility tokens to pay for services or products within the platform. In some cases, holding a certain amount of tokens may also provide additional benefits or privileges.
- Community Participation: Some Blockchain projects involve utility token holders in decision-making processes. Token holders may have voting rights on platform developments, upgrades, or other governance-related matters.
- Promoting Ecosystem Growth: Utility tokens play a role in promoting the growth of the Blockchain ecosystem by incentivizing users to participate actively. This can contribute to the overall success and sustainability of the platform.
Above discussed are the roles of the Utility token, which it can perform efficiently, and below, we are going to learn about the issues and challenges it holds.
Utility Token Issues and Challenges
Utility tokens are a good option for gaining profits and getting finances for new developing projects. However, it can provide some risks too. The Utility tokens became popular with the ICO boom in 2017. This was due to the excessive use of the utility token mechanisms. Also, the next year this reason dragged them down, causing trust issues and constant audits of the new projects.
The main reason which caused this fall was the projects had unrealistic goals, and the tokens were not regulated like the Security tokens. Therefore, it is necessary that the project must have real utility.
Problems that utility tokens face are as follows:
- Regulatory Uncertainty: The regulatory environment for utility tokens is often unclear and varies across jurisdictions. Determining whether a utility token qualifies as a security or not can be challenging, leading to legal risks for both issuers and investors.
- Investor Protection: Utility token sales, particularly Initial Coin Offerings (ICOs), have been associated with scams and fraudulent activities. Investors may face challenges in distinguishing legitimate projects from fraudulent ones, leading to potential financial losses.
- Volatility: The value of utility tokens can be highly volatile. Factors such as market sentiment, demand for the associated services, and overall market conditions can contribute to significant price fluctuations, impacting the token’s value.
- Lack of Intrinsic Value: Unlike some other cryptocurrencies like Bitcoin, utility tokens often lack intrinsic value. Their value is directly tied to the success and adoption of the associated platform, making them more susceptible to market sentiment.
- Market Saturation: The market for utility tokens has become crowded, making it challenging for new projects to stand out. This saturation can lead to difficulties in fundraising and attracting users to the platform.
- Technology Risks: Utility tokens often rely on underlying Blockchain technology. Issues such as scalability, security vulnerabilities, and technological advancements can impact the functionality and viability of the platform, affecting the utility token’s value.
- Limited Adoption: The success of utility tokens depends on the widespread adoption of the associated platform. If the platform fails to gain traction or faces competition from similar projects, the utility token’s value and utility may be compromised.
- Lack of Interoperability: In some cases, utility tokens are limited to use within a specific platform, hindering interoperability with tokens from other projects. This lack of interoperability can limit the token’s utility and potential partnerships.
- Governing Challenges: Decentralized governance mechanisms, which involve token holders in decision-making processes, can face challenges such as voter apathy, manipulation, or conflicts of interest among stakeholders.
- Technological Barriers for Users: Some potential users may face challenges in understanding and using utility tokens, especially if they are not familiar with Blockchain technology. Improving user interfaces and education is crucial for broader adoption.
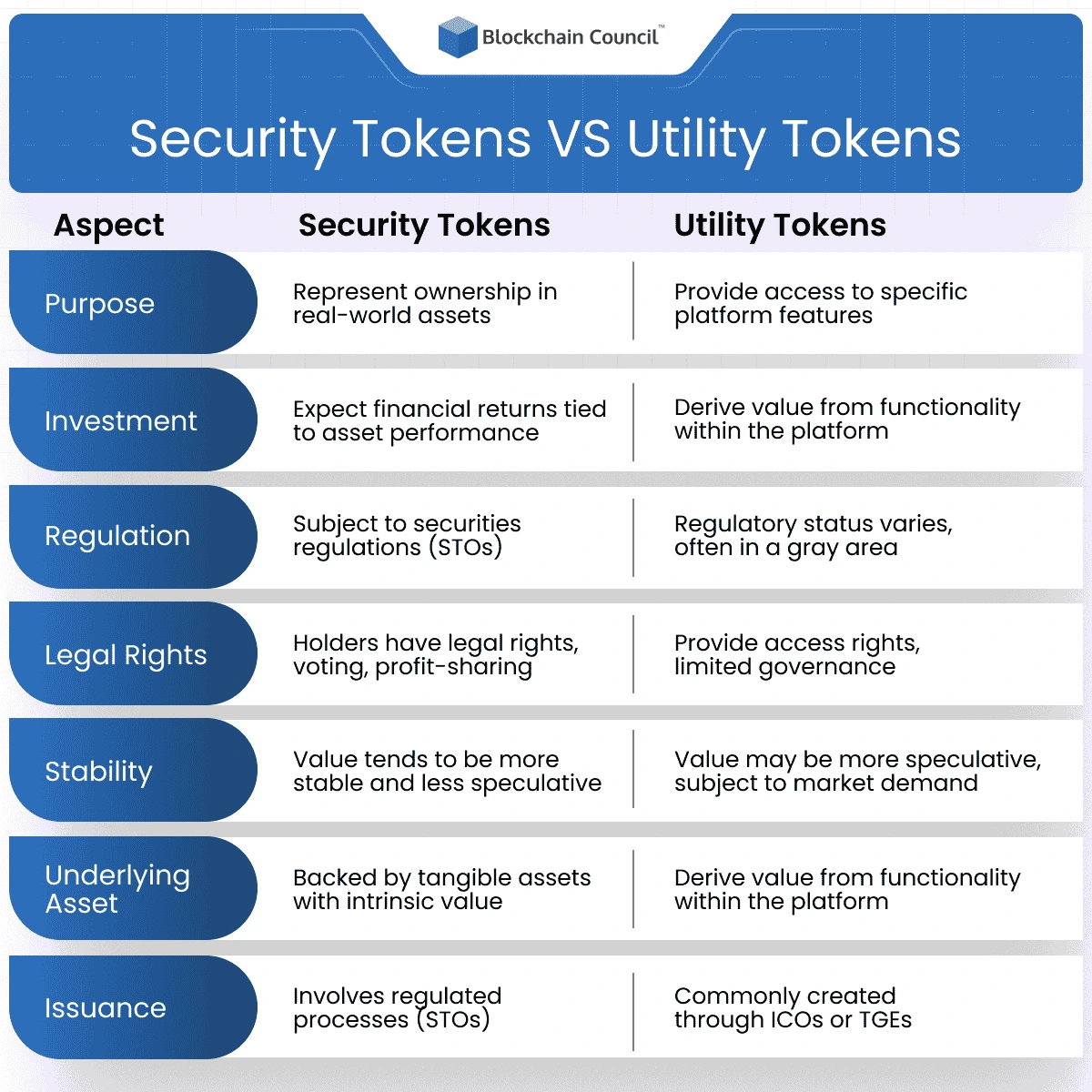
Security Tokens vs Utility Tokens
Security Tokens and Utility Tokens can be differentiated on the basis of the following points:
Purpose:
Security Tokens:
- Purpose: Security tokens serve as a digital representation of ownership or investment in real-world assets. They can represent shares in a company, ownership of real estate, or participation in other financial instruments.
- Investment: Investors in security tokens expect returns based on the performance of the underlying asset. This may include dividends, profit shares, or other financial benefits tied to the success of the asset.
Utility Tokens:
- Purpose: Utility tokens are designed to provide access to specific products, services, or functionalities within a Blockchain ecosystem. They act as a form of digital currency within the platform, enabling users to interact with its features.
- Functionality: The value of utility tokens is derived from the functionality they offer within the associated platform. Users acquire these tokens to unlock specific features, pay for services, or participate in activities facilitated by the Blockchain network.
Regulation:
Security Tokens:
- Compliance: Security tokens are subject to securities regulations in most jurisdictions. Issuers must adhere to legal frameworks to ensure compliance with investor protection measures.
- Issuance: The issuance of security tokens often involves regulated processes such as Security Token Offerings (STOs), ensuring that the token conforms to securities laws.
- Howey Test: The regulatory landscape for security tokens includes a more structured evaluation, often involving the Howey Test. This test helps determine whether an investment contract exists, impacting the regulatory classification of the token.
Utility Tokens:
- Regulatory Status: Utility tokens operate in a regulatory gray area, and their classification can vary. Some may be classified as securities, while others may be considered commodities or have a distinct regulatory status.
- Issuance: Utility tokens are commonly created through Initial Coin Offerings (ICOs) or Token Generation Events (TGEs), which may not always be subject to the same level of regulatory oversight as security token offerings.
- Howey Test: Utility tokens may not always undergo the same scrutiny as security tokens regarding the Howey Test, as the regulatory focus may differ based on the specific characteristics and usage of the token.
Rights and Benefits:
Security Tokens:
- Legal Rights: Holders of security tokens have legal rights associated with ownership. This may include voting rights in corporate decisions, profit-sharing, or other privileges tied to the underlying asset.
- Stability: The value of security tokens tends to be more stable and less speculative compared to utility tokens, as it is often tied to the performance of tangible assets.
Utility Tokens:
- Access Rights: Utility token holders have access to specific features or services within the Blockchain platform. However, they typically do not have traditional ownership rights in the company or project.
- Limited Governance: Some utility tokens offer limited governance rights, allowing holders to participate in decisions related to the development or upgrades of the platform.
Underlying Asset:
Security Tokens:
- Backing: Security tokens are typically backed by tangible assets with intrinsic value, such as shares in a company, real estate, or other financial instruments.
Utility Tokens:
- Functional Value: Utility tokens derive their value from the functionality they provide within the associated platform. Their value is linked to the demand for the services or products offered by the Blockchain ecosystem.
Issuance:
Security Tokens:
- Regulated Processes: Security tokens are issued through regulated processes, ensuring compliance with securities laws. This often involves thorough legal and compliance procedures.
Utility Tokens:
- ICO or TGE: Utility tokens are commonly created through Initial Coin Offerings (ICOs) or Token Generation Events (TGEs). These events may have less stringent regulatory requirements compared to security token offerings.
Real Life Examples of Security Tokens and Utility Tokens
Security Tokens:
- Polymath (STO): Polymath is a platform designed to simplify the creation and issuance of security tokens, having secured over $50 million in funding. Notable partners include Fidelity Investments and Blockchain Capital.
- RealBlocks (Real Estate Tokens): RealBlocks specializes in the tokenization of real estate properties and has successfully raised over $10 million in funding. The company has established partnerships with prominent real estate developers such as Hines and Tishman Speyer.
- WeWork (Equity Tokens): WeWork, a provider of coworking spaces, has announced plans to issue security tokens as a means of raising capital for its operations.
- BlockVC (Debt Tokens): BlockVC, a company offering debt financing to early-stage Blockchain enterprises, has successfully raised over $25 million in funding and has issued debt tokens to various investors.
Utility Tokens:
- Tether (USDT – Stablecoin): Tether (USDT) is the most widely used stablecoin, pegged to the US dollar. It serves as both a medium of exchange and a store of value in various transactions.
- MakerDAO (MKR – Governance Tokens): MakerDAO operates as a decentralized autonomous organization (DAO) and issues the DAI stablecoin. MKR token holders possess voting rights within the DAO, enabling them to influence project decisions.
- Filecoin (FIL – Access Tokens): Filecoin utilizes FIL tokens as access tokens within its decentralized storage network. Users holding FIL tokens can not only contribute storage space but also access the network’s storage services.
- Basic Attention Token (BAT – Payment Tokens): Basic Attention Token (BAT) functions on the Brave web browser, where users can earn BAT by viewing ads. These tokens can be utilized to tip content creators or make various online purchases.
Conclusion
The choice between Security Tokens and Utility Tokens depends on specific use cases, regulatory considerations, and the desired functionality within a Blockchain ecosystem. Security Tokens offer a regulated and compliant avenue for investment, mirroring traditional financial instruments. On the other hand, Utility Tokens provide a means for accessing specific services or functionalities within a Blockchain network.
As the crypto space matures, continued scrutiny and adaptation of regulations will likely shape the landscape, influencing the prominence and utility of both Security and Utility Tokens. Investors and developers alike should stay informed and navigate these choices with a clear understanding of their objectives and the evolving regulatory environment.
Hope this article helped you understand the basic differences between a security token, and utility token. We have now learned that one helps incentivize holders to act in a certain way while the other is a contract representing the legal ownership of an asset. But out of these two, security tokens are considered safer than utility tokens due to the strict regulations imposed upon them. To read more such Blockchain-related articles, visit Blockchain Council.
If you want to keep up with the trends of the Blockchain industry, join our communities on Discord, Reddit and Telegram.
Frequently Asked Questions
- A security token is a digital asset representing ownership or investment in real-world assets like shares in a company, real estate, or financial instruments.
- Security tokens are subject to federal securities laws and regulations to ensure compliance.
- A utility token is a type of cryptocurrency created during Initial Coin Offerings (ICOs) or Token Generation Events (TGEs).
- Utility tokens provide access to specific products, services, or functionalities within a Blockchain ecosystem.
- They are not considered investments and are generally exempt from federal securities laws if properly set up.
What is the difference between utility token and security token?
- Purpose: Security tokens represent ownership or investment, while utility tokens provide access to platform features.
- Regulation: Security tokens are subject to securities regulations, while utility tokens operate in a regulatory gray area.
- Rights and Benefits: Security tokens offer legal rights and stability, while utility tokens grant access rights and have limited governance.
- Underlying Asset: Security tokens are backed by tangible assets, while utility tokens derive value from platform functionality.
- Issuance: Security tokens follow regulated processes, whereas utility tokens are commonly created through ICOs or TGEs.
What is an example of a utility token?
- Examples of utility tokens include Filecoin, Tether, and MakerDAO.
- These tokens are created during crowd sales and grant access to discounted fees or special features within a Blockchain platform.
What is an example of a security token?
- Examples of security tokens include Polymath, RealBlocks, and WeWork.
- Security tokens typically represent ownership in assets like shares, real estate, or financial instruments, and compliance with securities laws is a crucial aspect.




































































 Guides
Guides News
News Blockchain
Blockchain Cryptocurrency
& Digital Assets
Cryptocurrency
& Digital Assets Web3
Web3 Metaverse & NFTs
Metaverse & NFTs
